requests,js逆向练习
自上而下排除jquery源码,点进去utils
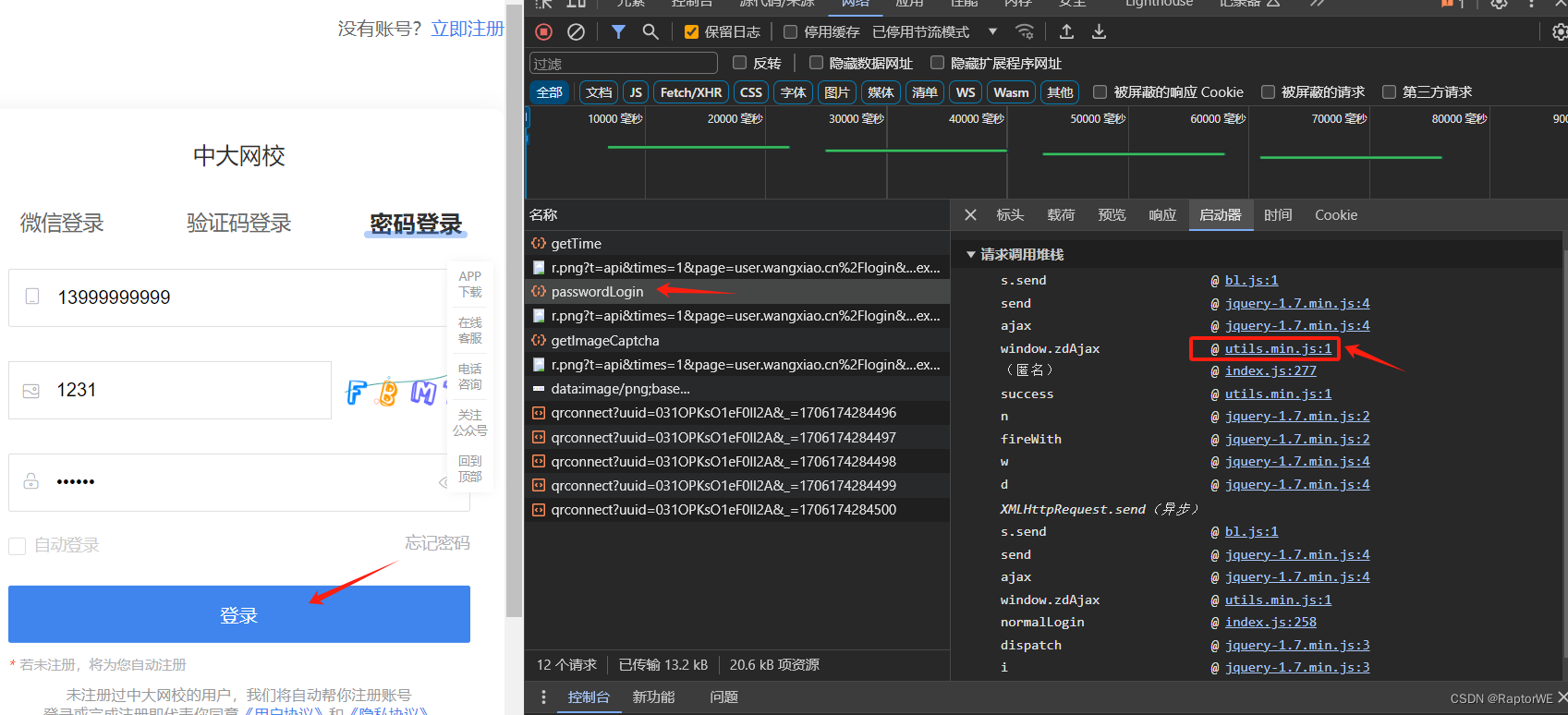
发现第一次请求是getTime
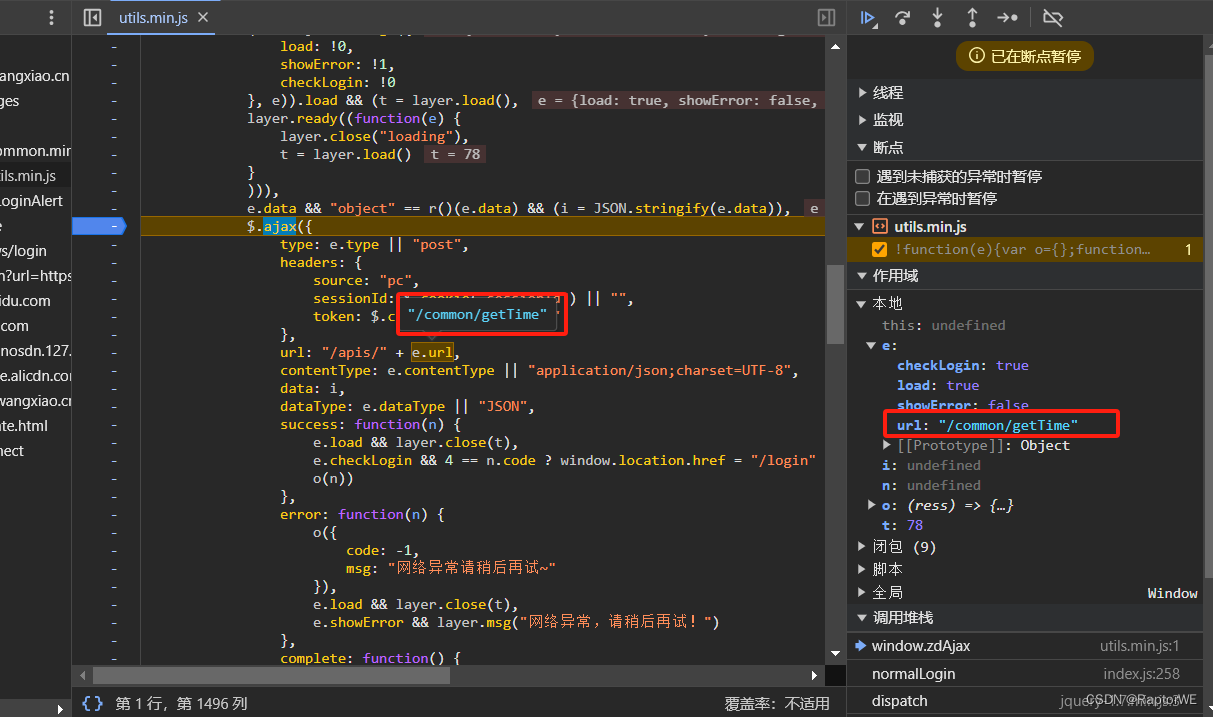
再次运行此断点才是登录,这个时候密码已经被加密了
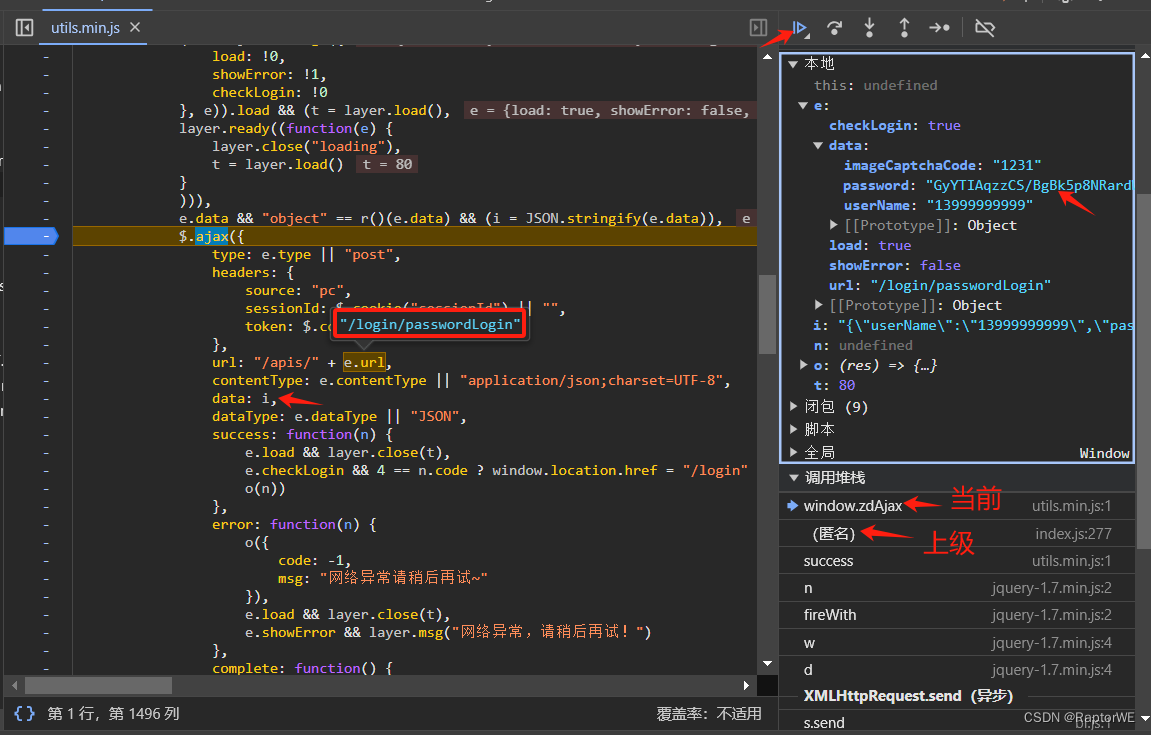
查看上级js页面,发现加密函数
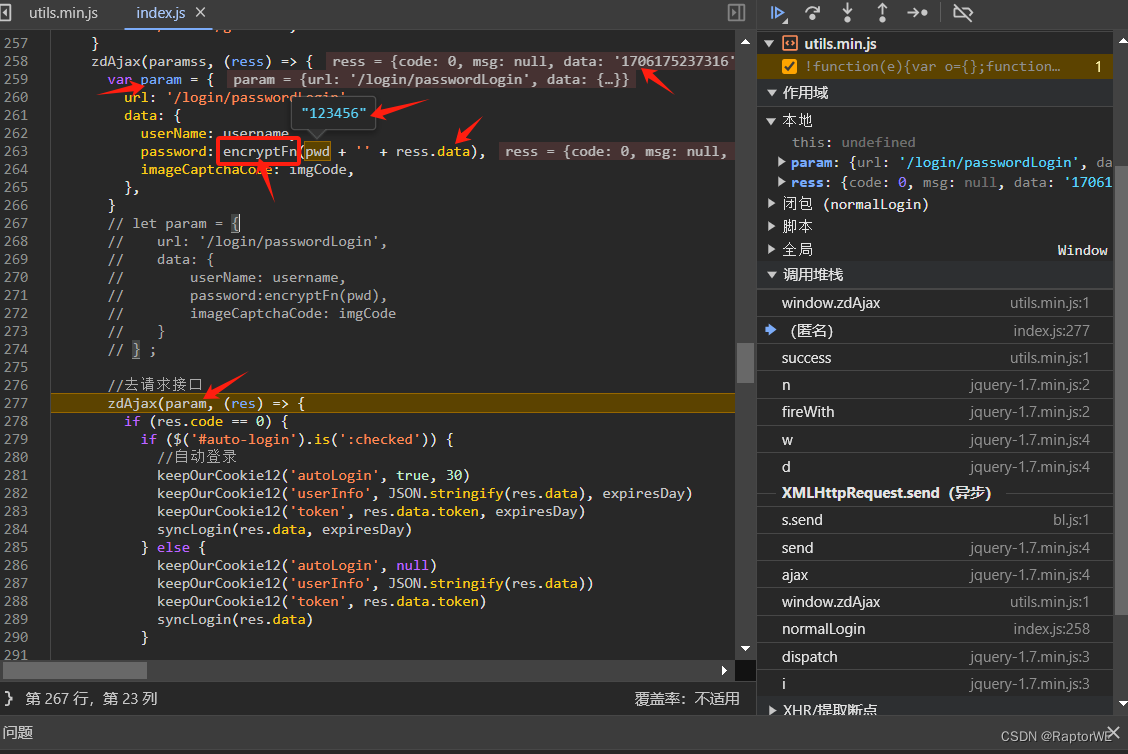
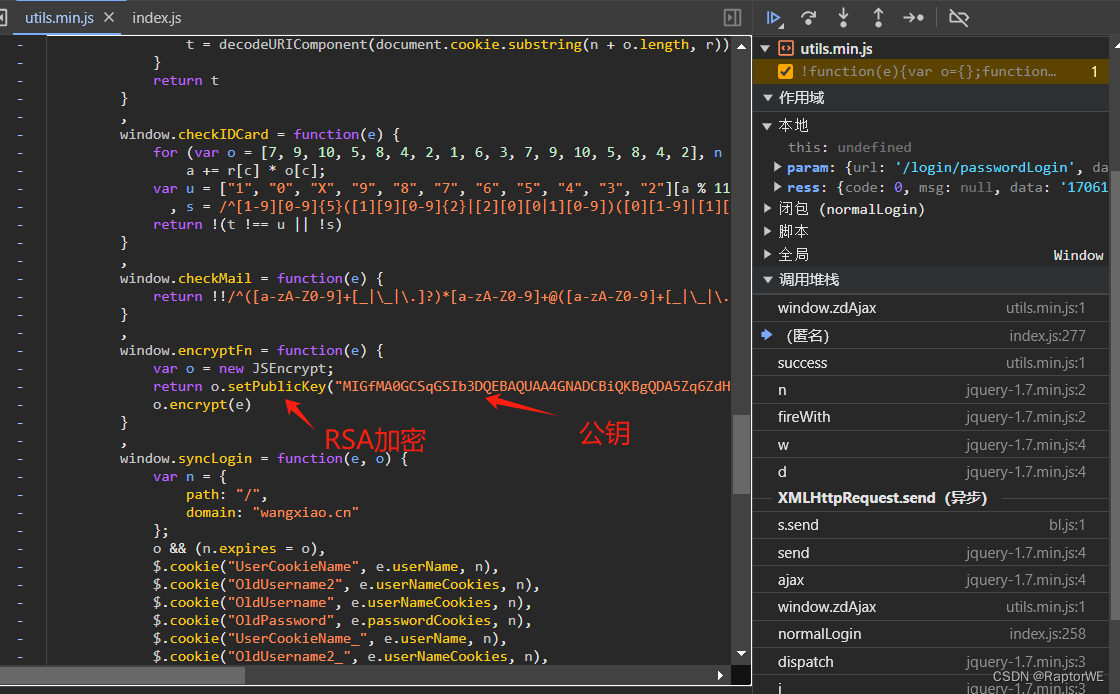
进去看函数加密过程
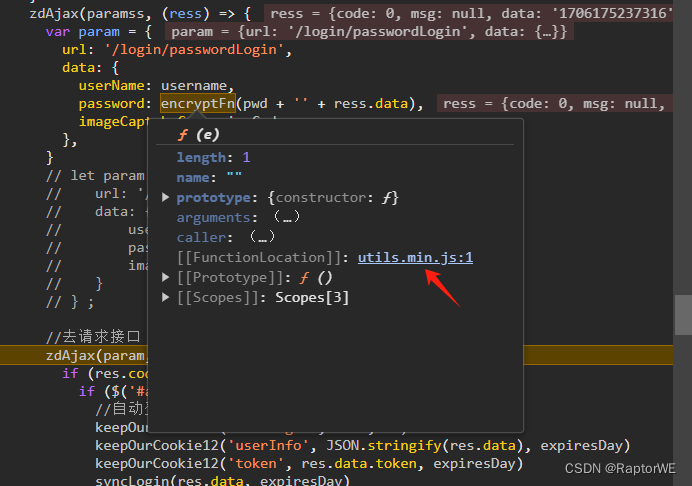
得到结果RSA
python代码
import base64
import json
import requests
from fake_useragent import UserAgent
from Crypto.Cipher import PKCS1_v1_5
from Crypto.PublicKey import RSA
from spider_WE.utils.tujian import crack_code_img_b64
username = '账号'
password = '密码'
headers = {
'User-Agent': UserAgent().random,
'Content-Type': 'application/json; charset=utf-8'
}
# 1.进入登录页->加载cookie
session = requests.session()
resp = session.get('https://user.wangxiao.cn/login')
# 2.获取验证码->打码平台
verify_code_url = 'https://user.wangxiao.cn/apis//common/getImageCaptcha'
verify_resp = session.post(verify_code_url, headers=headers)
verify_data = verify_resp.json()
verify_b64_img = verify_data['data'].split('base64,')[-1]
verify_code = crack_code_img_b64(verify_b64_img, 3)
# 3.把密码加密
get_time_url = 'https://user.wangxiao.cn/apis//common/getTime'
get_time_resp = session.post(get_time_url, headers=headers)
get_time_data = get_time_resp.json()['data']
pwd = password + str(get_time_data)
pub_key = 'MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDA5Zq6ZdH/' \
'RMSvC8WKhp5gj6Ue4Lqjo0Q2PnyGbSkTlYku0HtVzbh3S9F9oHbxeO55E8tEEQ5wj/' \
'+52VMLavcuwkDypG66N6c1z0Fo2HgxV3e0tqt1wyNtmbwg7ruIYmFM+dErIpTiLRDvOy+0vgPcBVDfSUHwUSgUtIkyC47UNQIDAQAB'
rsa_key = RSA.import_key(base64.b64decode(pub_key))
# 加密
rsa = PKCS1_v1_5.new(rsa_key)
crypto = rsa.encrypt(pwd.encode('utf-8'))
crypto_pwd = base64.b64encode(crypto).decode('utf-8')
# 4.登录
login_url = 'https://user.wangxiao.cn/apis//login/passwordLogin'
login_data = {
'imageCaptchaCode': verify_code,
'password': crypto_pwd,
'userName': username
}
login_resp = session.post(login_url, data=json.dumps(login_data), headers=headers)
login_info = login_resp.json()['data']
# 5.对登录后的cookie信息进行整理
cookie_dic = {
"autoLogin": "null",
"OldPassword": login_info['passwordCookies'],
"OldPassword_": login_info['passwordCookies'],
"OldUsername": login_info['userNameCookies'],
"OldUsername_": login_info['userNameCookies'],
"OldUsername2": login_info['userNameCookies'],
"OldUsername2_": login_info['userNameCookies'],
f"{login_info['userName']}_exam": login_info['sign'],
"token": login_info['token'],
"UserCookieName": login_info['userName'],
"UserCookieName_": login_info['userName'],
"userInfo": login_info,
"sessionId": session.cookies.get("sessionId")
}
原文地址:https://blog.csdn.net/Ben_boba/article/details/135853060
免责声明:本站文章内容转载自网络资源,如本站内容侵犯了原著者的合法权益,可联系本站删除。更多内容请关注自学内容网(zxcms.com)!
